How to Easily Update IoT Device Firmware Remotely
Written by:

Kostiantyn Oliynyk
Head of IoT at Webbylab
With a robust academic background in Telecommunication Systems Engineering, I apply my knowledge to lead innovations in the IoT domain. Starting as the first team member in the newly formed IoT department at WebbyLab, I've spearheaded its growth, fostering the expansion into embedded and hardware development alongside our core software projects. My dedication lies in pushing the boundaries of IoT technology, fostering a culture of innovation and excellence that profoundly impacts our clients' operational success.
IoT devices typically have built-in software that can detect when a new version of the software is available. This can be done either automatically or manually, depending on the device. Some devices may also send notifications to the user when a new update is available.
To initiate a software update on an IoT device, you should first check the user manual or the manufacturer’s website for instructions. The process will typically involve connecting the device to a computer or mobile device and downloading the new software. Once the software is downloaded, you will need to install it on the device according to the instructions provided.
If your device is configured to receive updates over the air automatically, you do not need to initiate this process.
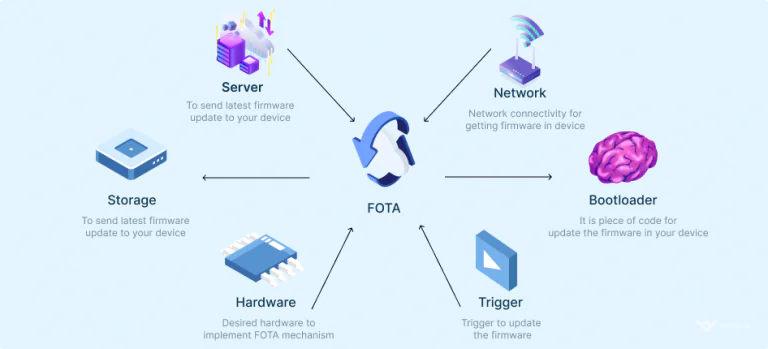
Future trends for updating software in IoT devices include over-the-air (OTA) updates, which allow devices to update their software without the need for a physical connection to a computer. This is expected to become more common as IoT devices become more sophisticated and are used in more advanced applications.
A promising technology is using blockchain in modular device updates using a gateway. Thanks to this solution, the blockchain ledger and smart contracts become resistant to network failures and cyberattacks.
Yes, an IoT software update can cause compatibility issues with other devices or systems. It is important to test the updated software before deploying it in a production environment to ensure that it works as expected and does not cause any compatibility issues.
When choosing a contractor to update IoT devices and software, it is important to look for a company with experience in IoT development and software updates. You should also consider the contractor’s reputation, references, and certifications. Additionally, you should ask about the contractor’s approach to testing and quality assurance to ensure that the updates are reliable and do not cause compatibility issues.
The frequency of your IoT device firmware updates depends on various factors. Those include the device type, functionality, potential security risks, user expectations, and manufacturer recommendations. For example, a smart thermostat, a complex solution, requires more frequent updates than a simple smart light bulb. Generally, you should stay informed of the available updates and install them promptly.
To update your IoT device’s firmware, follow the manufacturer’s provided instructions. Choose the update type, e.g., manual or automatic OTA, and install the necessary upgrades. Finally, test the changes properly before deploying your device.










![Firmware Analysis for IoT Devices [Practical Guide]](https://webbylab.com/wp-content/uploads/2022/12/firmware-analysis-768x260.png)
![Difference Between Arduino and Raspberry Pi [with Comparison Table]](https://webbylab.com/wp-content/uploads/2024/06/upload_66701d6ab7438-768x260.png)
