IoT Security: Risks, Examples, and Solutions
Written by:

Kostiantyn Oliynyk
Head of IoT at Webbylab
With a robust academic background in Telecommunication Systems Engineering, I apply my knowledge to lead innovations in the IoT domain. Starting as the first team member in the newly formed IoT department at WebbyLab, I've spearheaded its growth, fostering the expansion into embedded and hardware development alongside our core software projects. My dedication lies in pushing the boundaries of IoT technology, fostering a culture of innovation and excellence that profoundly impacts our clients' operational success.
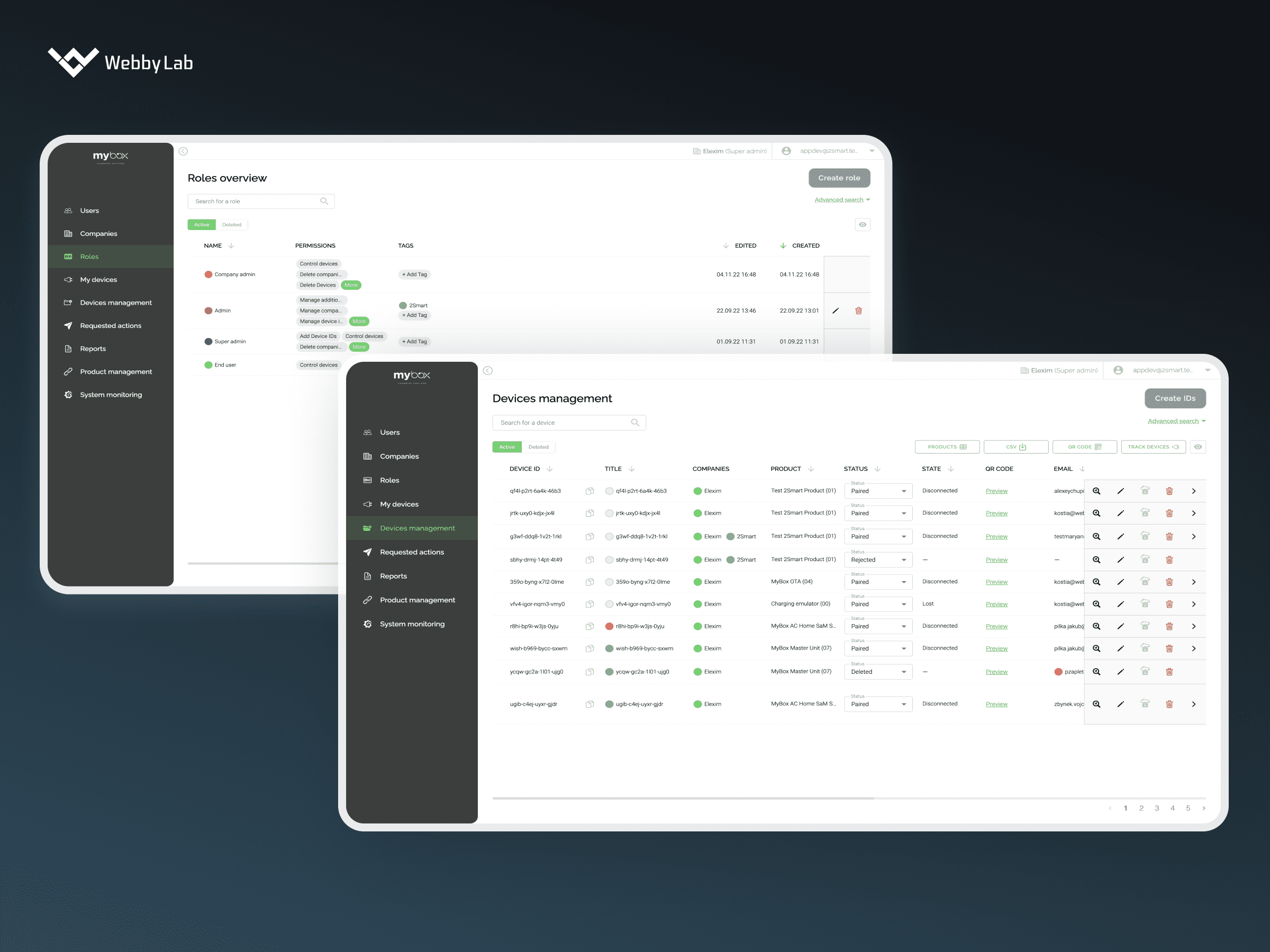
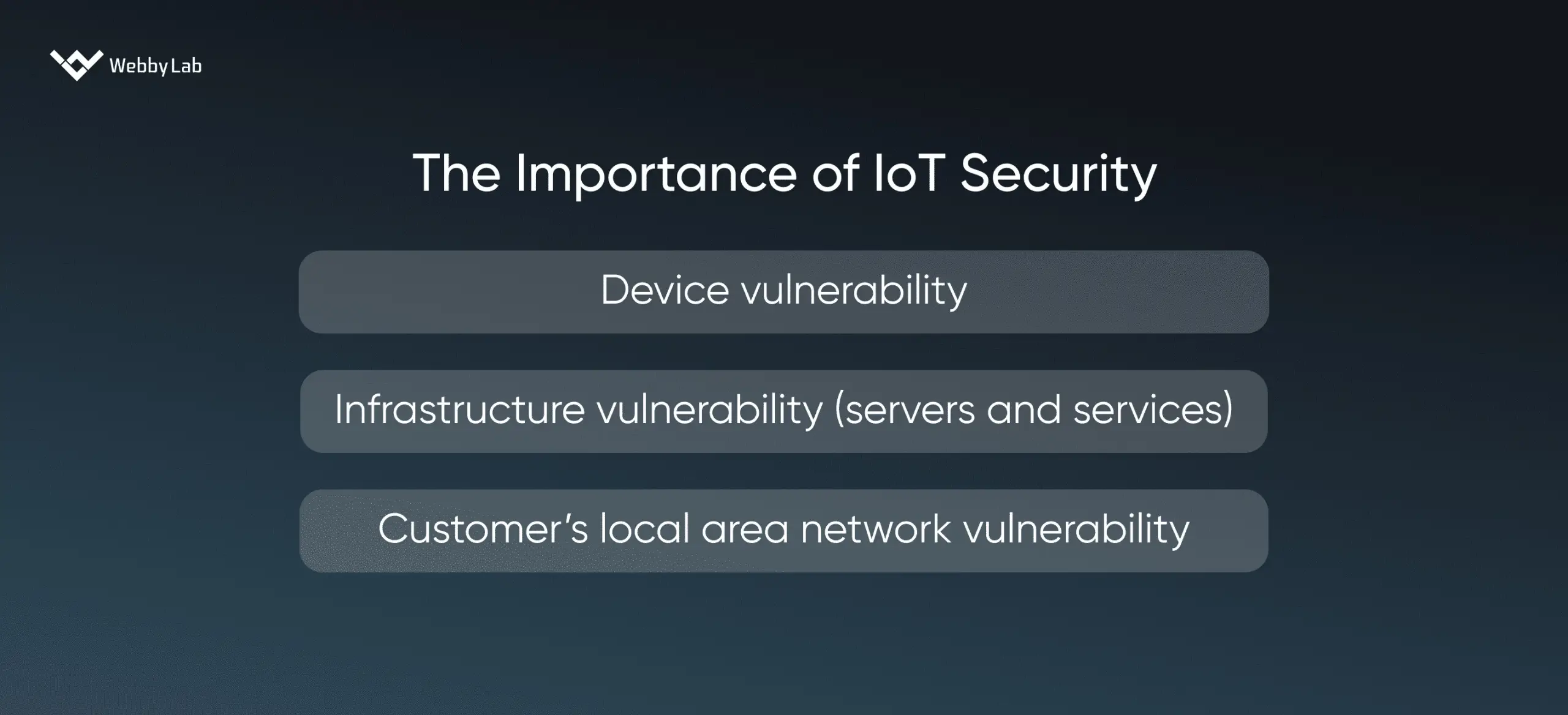
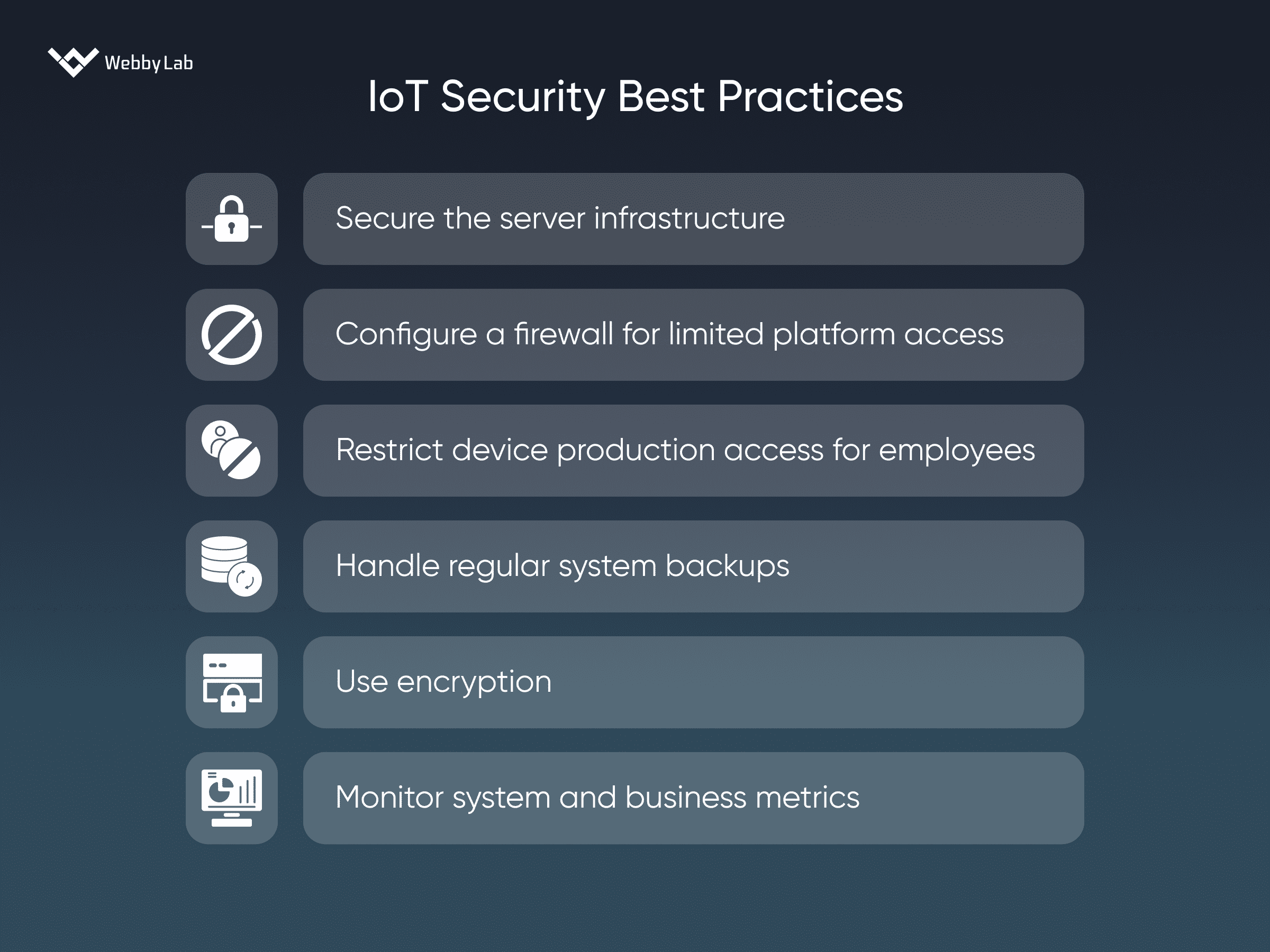
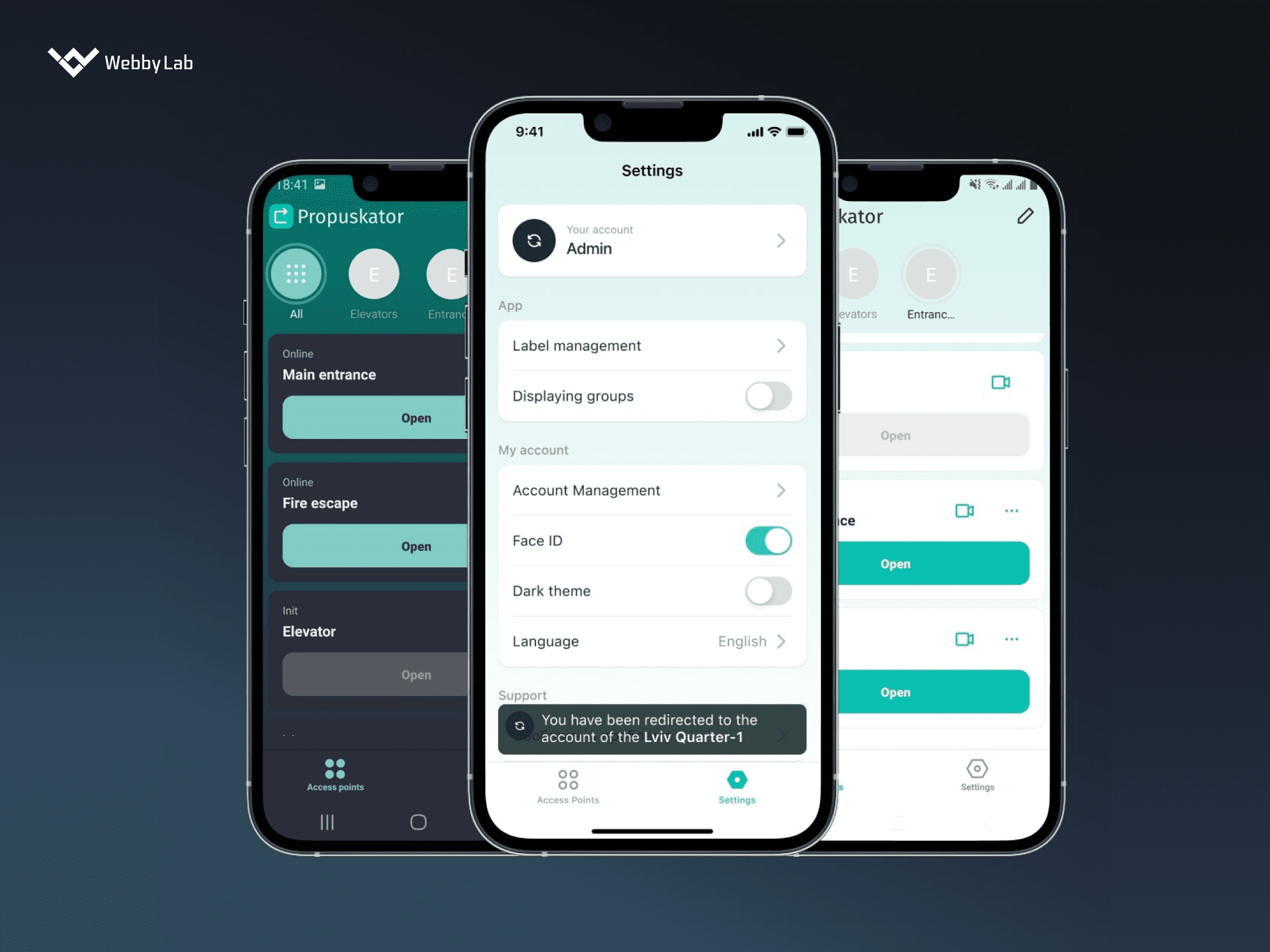
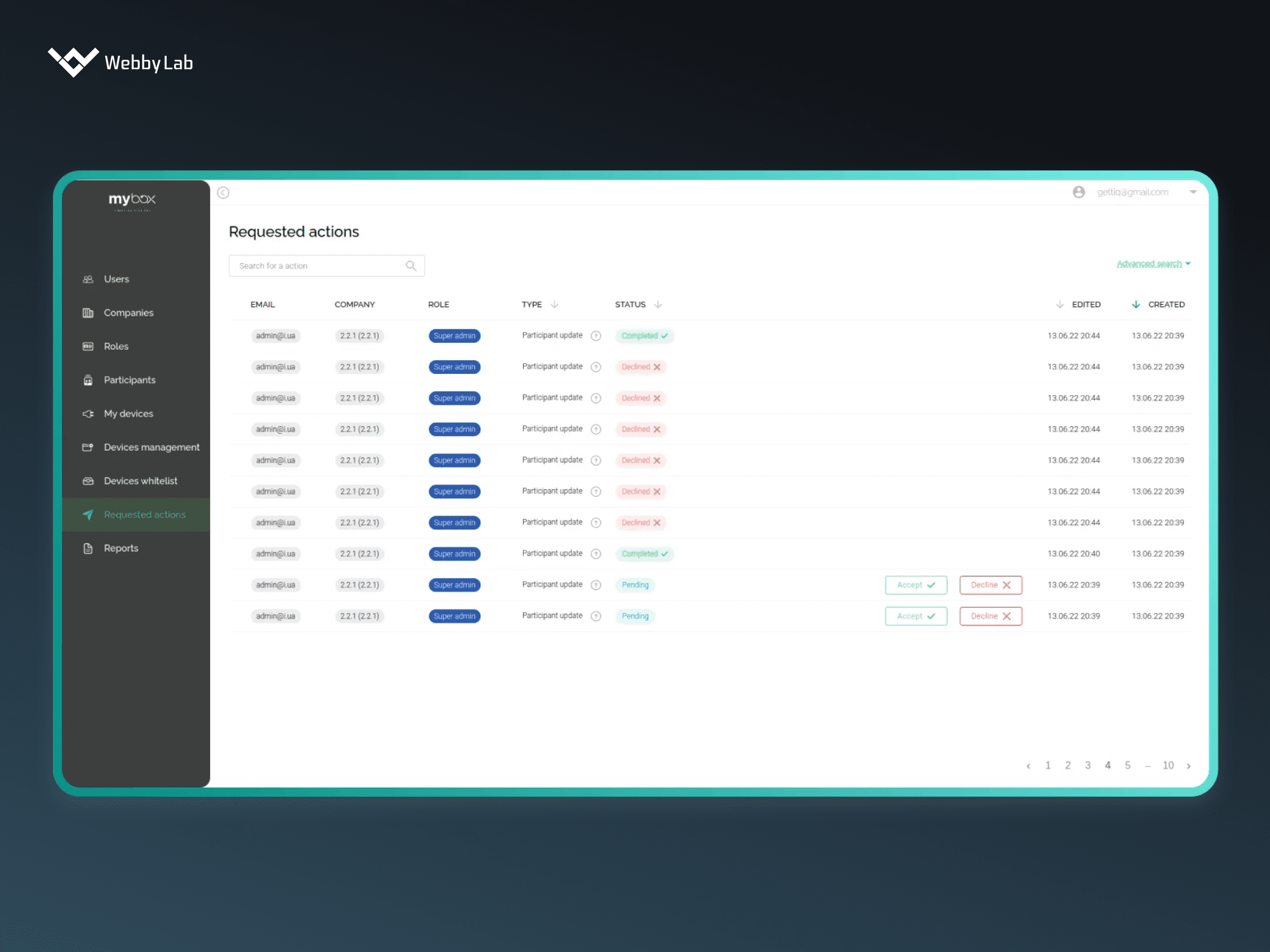
IoT devices security is important since these devices are typically interconnected, transmit sensitive data, and control critical functions. A single data breach or a cyber attack can lead to reputational and financial damage and disruption of processes.
The main Internet of Things security issues include weak authentication, legacy assets, device diversity, outdated software and firmware, privacy concerns, and other threats that may lead to data leakage and IoT system shutdown.
ISO/IEC 27001, ISO/IEC 27002, and ISO/IEC 27005 are the core standards that regulate IoT security requirements. Additional laws include the General Data Protection Regulation (GDPR) that oversees proper data protection in the European Union.
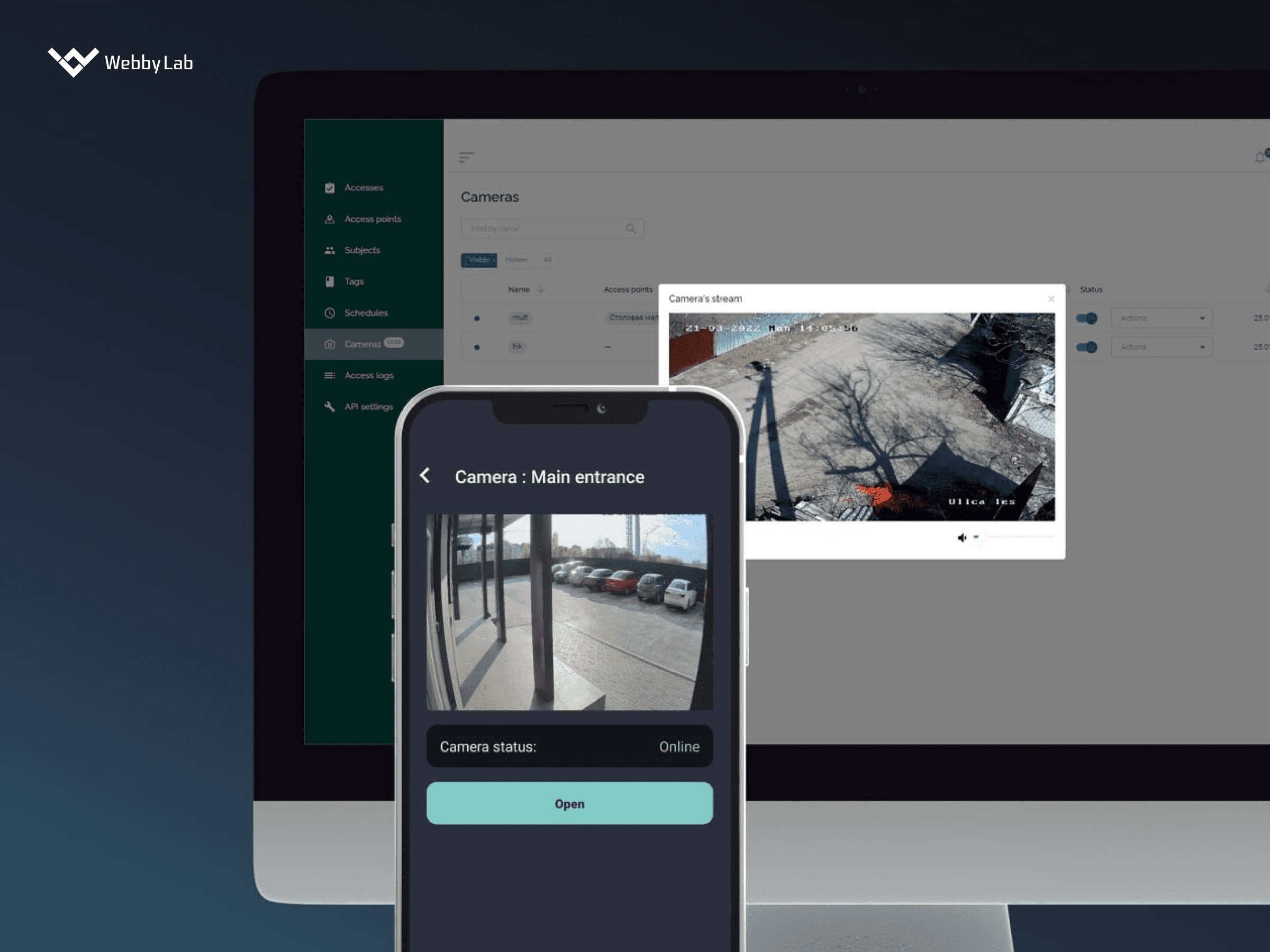
Generally, industries heavily reliant on IoT are most exposed to security risks. Those include industrial IoT (IIoT), healthcare, manufacturing, and critical infrastructure.
Using blockchain tech for secure data transfer and AI and ML for threat detection are the most prominent innovations in IoT security. Reliance on zero-trust architectures is a security trend as well.