SaaS vs PaaS vs IaaS: Finding the Best Fit for Your IoT Project
Written by:

Kostiantyn Oliynyk
Head of IoT at Webbylab
With a robust academic background in Telecommunication Systems Engineering, I apply my knowledge to lead innovations in the IoT domain. Starting as the first team member in the newly formed IoT department at WebbyLab, I've spearheaded its growth, fostering the expansion into embedded and hardware development alongside our core software projects. My dedication lies in pushing the boundaries of IoT technology, fostering a culture of innovation and excellence that profoundly impacts our clients' operational success.
FAQ
Can I change my cloud model after deployment?
Generally, yes. However, the transitioning process can be complex, given the need for data migration and IoT architecture redesign.
What are the hidden costs in SaaS vs. IaaS vs. PaaS?
In the SaaS cloud services, you have to deal with subscription fees, in IoT PaaS, you pay for development tools and scaling, and in IaaS — for resource usage, maintenance, and infrastructure upgrades.
Which cloud model works best for infrastructure-heavy IoT projects?
IaaS is perfect for infrastructure-heavy projects, like smart cities or industrial settings.
How does WebbyLab ensure IoT solution security?
We implement encryption, multi-layer authentication, and access controls within your cloud architecture. Whether you’re working with Azure, AWS, or GCP — we ensure security following your needs.
What’s the cost of implementing IoT solutions using cloud models?
Costs can vary significantly based on your project’s scale, the chosen cloud platform, and the model (SaaS, PaaS, IaaS). Discover accurate pricing by contacting our team.
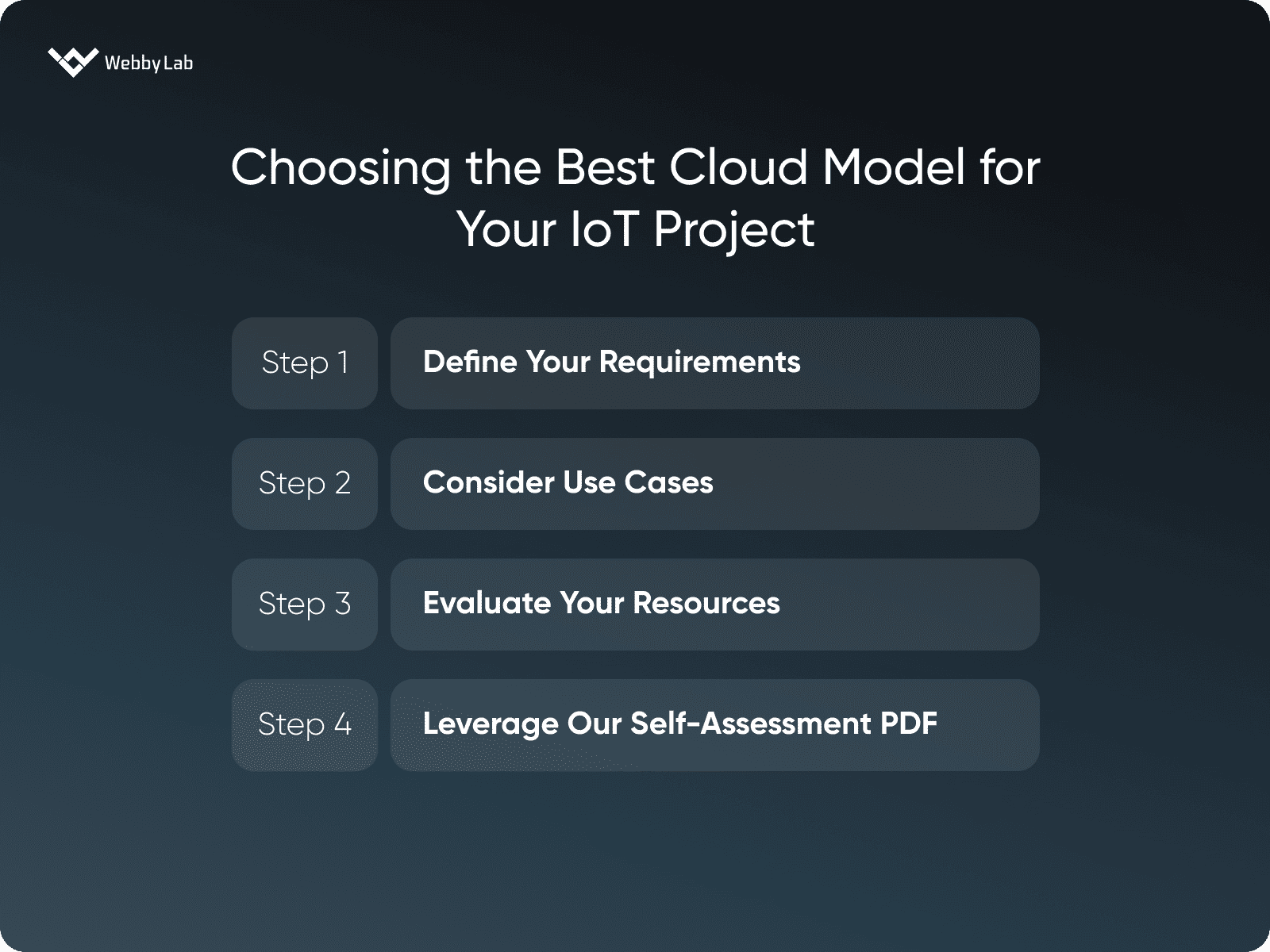
How do I choose the right cloud model for my IoT project?
To choose the right cloud platform, analyze your project’s goals, technical resources, budget, and customization needs. Also, check our self-assessment document to make your final decision.
How do security features vary across IaaS, PaaS, and SaaS for your IoT project?
IaaS cloud deployment requires you to manage most of the security aspects yourself. PaaS architecture balances security responsibilities between you and the provider, while IoT SaaS security is largely managed by the vendor.
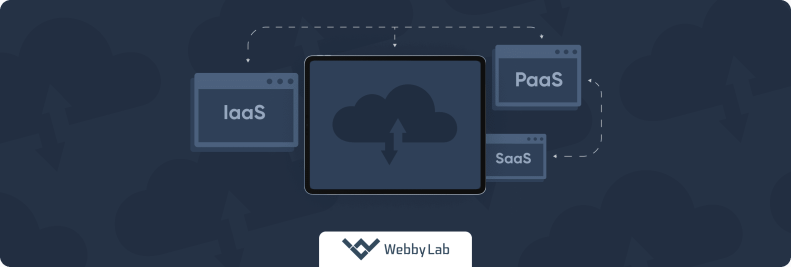
Which cloud model is best for IoT?
It depends on your needs:
1. SaaS (like Azure IoT Central) is best for businesses that want an easy, plug-and-play platform for device monitoring and analytics without dealing with infrastructure management.
2. PaaS (like AWS IoT Core) offers more flexibility for developers building custom apps while still using cloud infrastructure.
3. IaaS examples (like Google Cloud Compute Engine) are ideal for enterprises needing full control over data, scalability, and security.
Custom development works for companies with unique security, compliance, or integration needs, though it requires higher investment and ongoing maintenance.
Can I switch from SaaS to PaaS?
Yes, but it’s not always easy. Migrating from SaaS to PaaS means transferring data, rebuilding application logic, and creating new integrations. This requires technical expertise and careful planning. A hybrid approach — keeping core functions on SaaS while gradually shifting to PaaS — can help minimize risks and downtime.
What are the security concerns with IoT cloud services?
Security is critical in IoT cloud services, as these platforms store and process large volumes of sensitive data. Key risks include:
1. Unauthorized access and data breaches — strong authentication and encryption are a must.
2. Lack of end-to-end encryption — some platforms are vulnerable to cyberattacks.
3. DDoS attacks — compromised IoT devices can be exploited.
4. Cloud provider dependency — security gaps may arise if providers don’t update patches or compliance measures.
To stay secure, choose providers with strong security certifications (ISO 27001, GDPR, CCPA), enforce role-based access control, and consider edge computing to process critical data closer to devices. Regular security audits and monitoring are also essential.
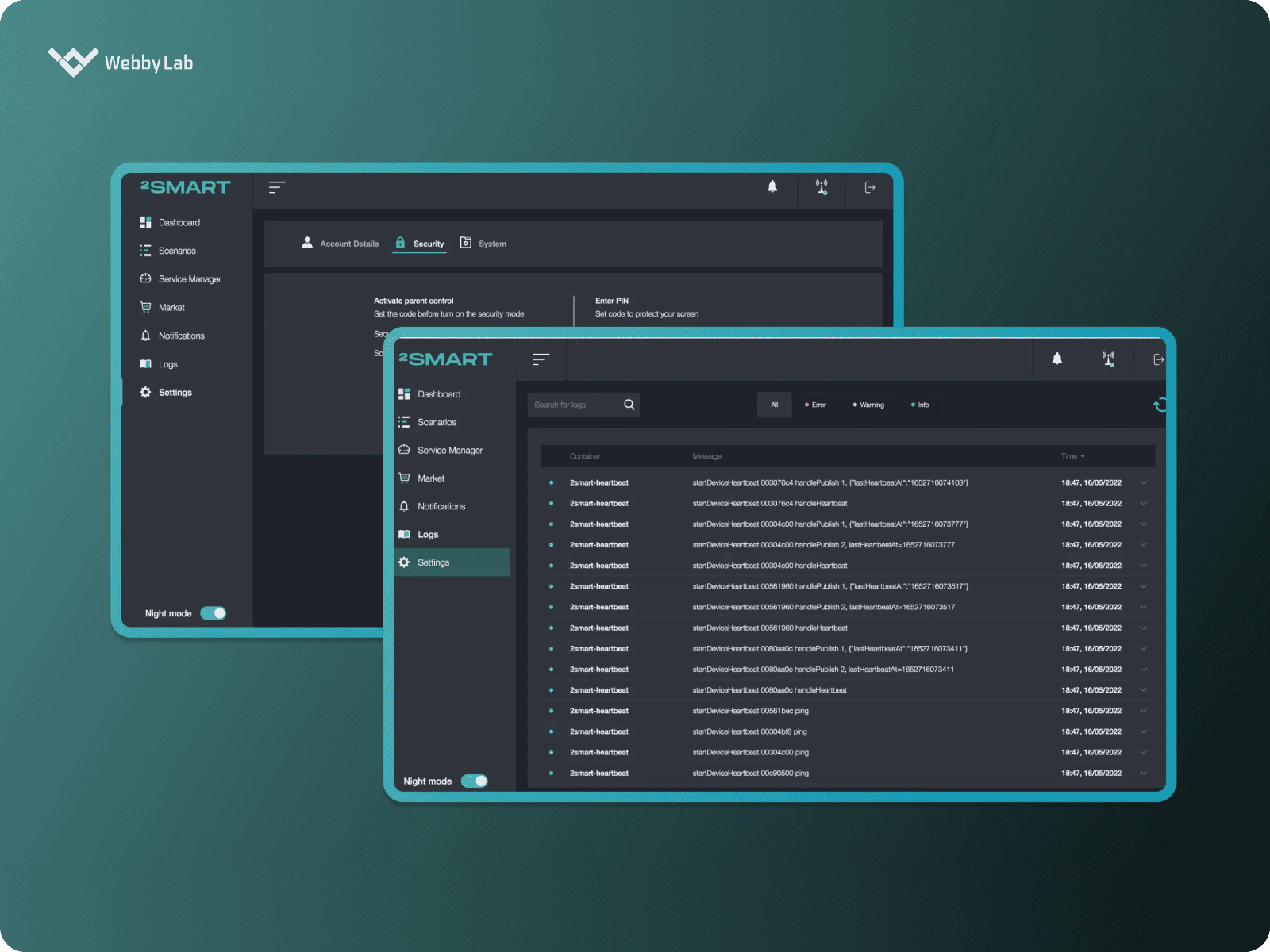 A 2Smart Standalone PaaS solution
A 2Smart Standalone PaaS solution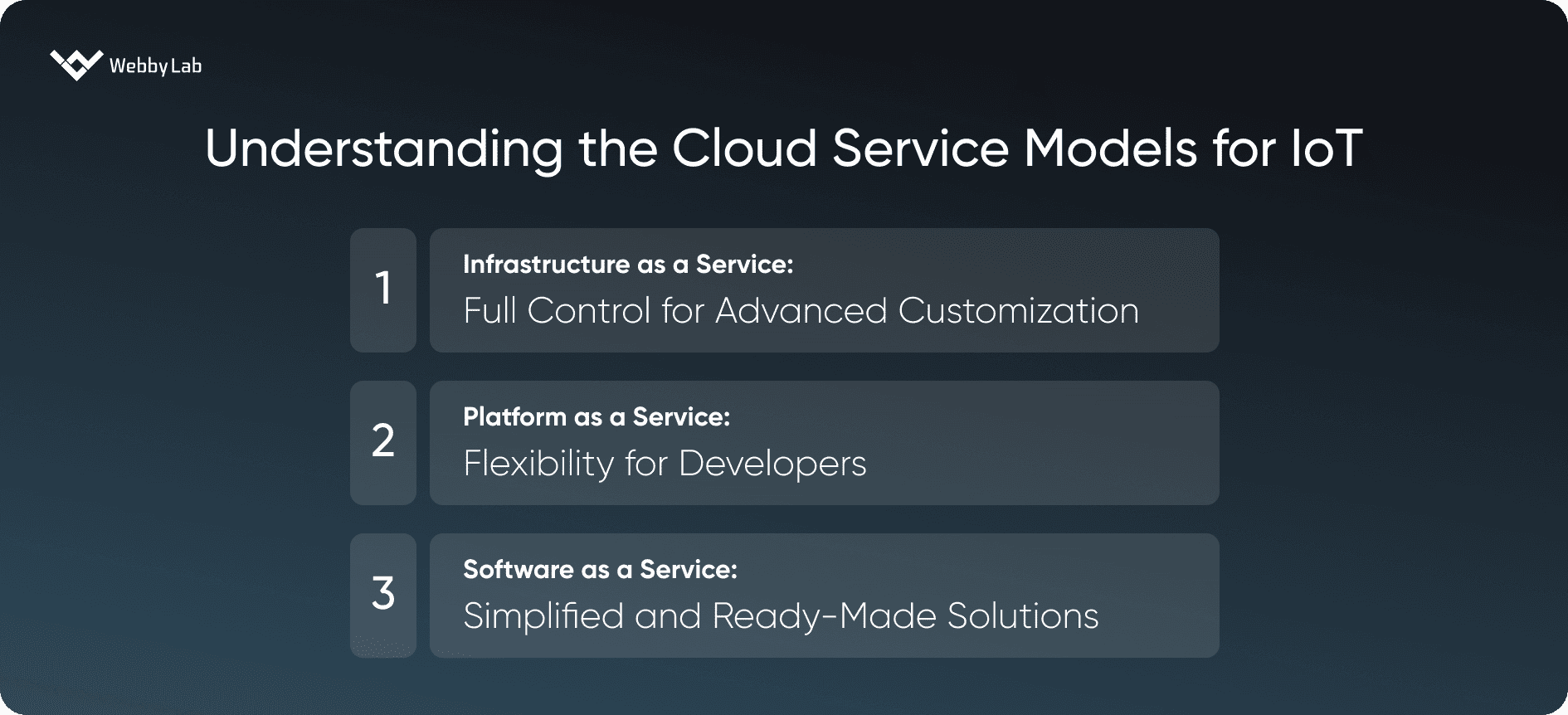
 A Propuskator mobile app
A Propuskator mobile app A 2Smart Cloud platform for device testing, deployment, and management
A 2Smart Cloud platform for device testing, deployment, and management A MyBox platform based on 2Smart Cloud
A MyBox platform based on 2Smart Cloud A Intellect platform based on 2Smart Cloud
A Intellect platform based on 2Smart Cloud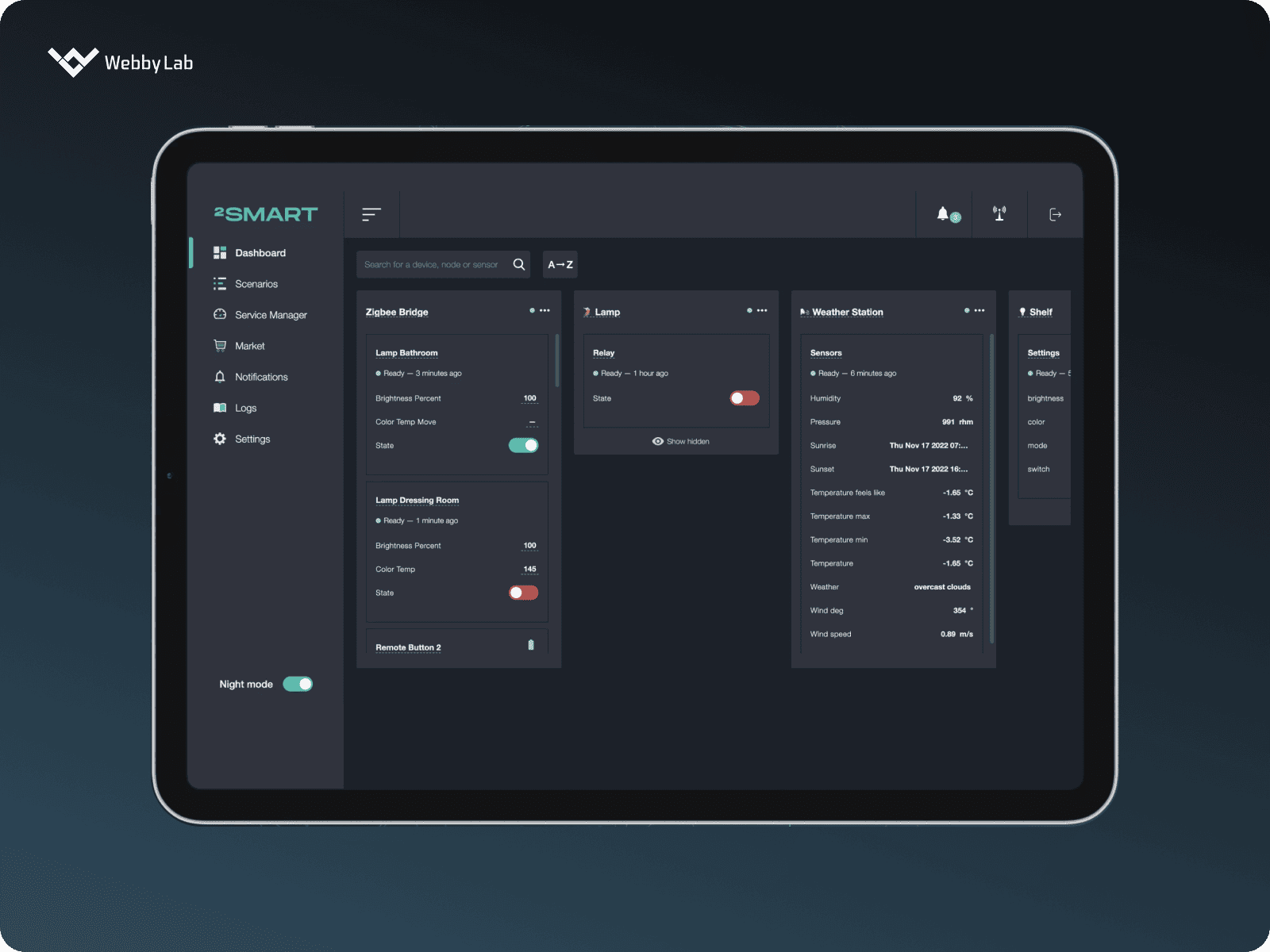 A 2Smart Standalone platform for IoT ecosystem control and automation
A 2Smart Standalone platform for IoT ecosystem control and automation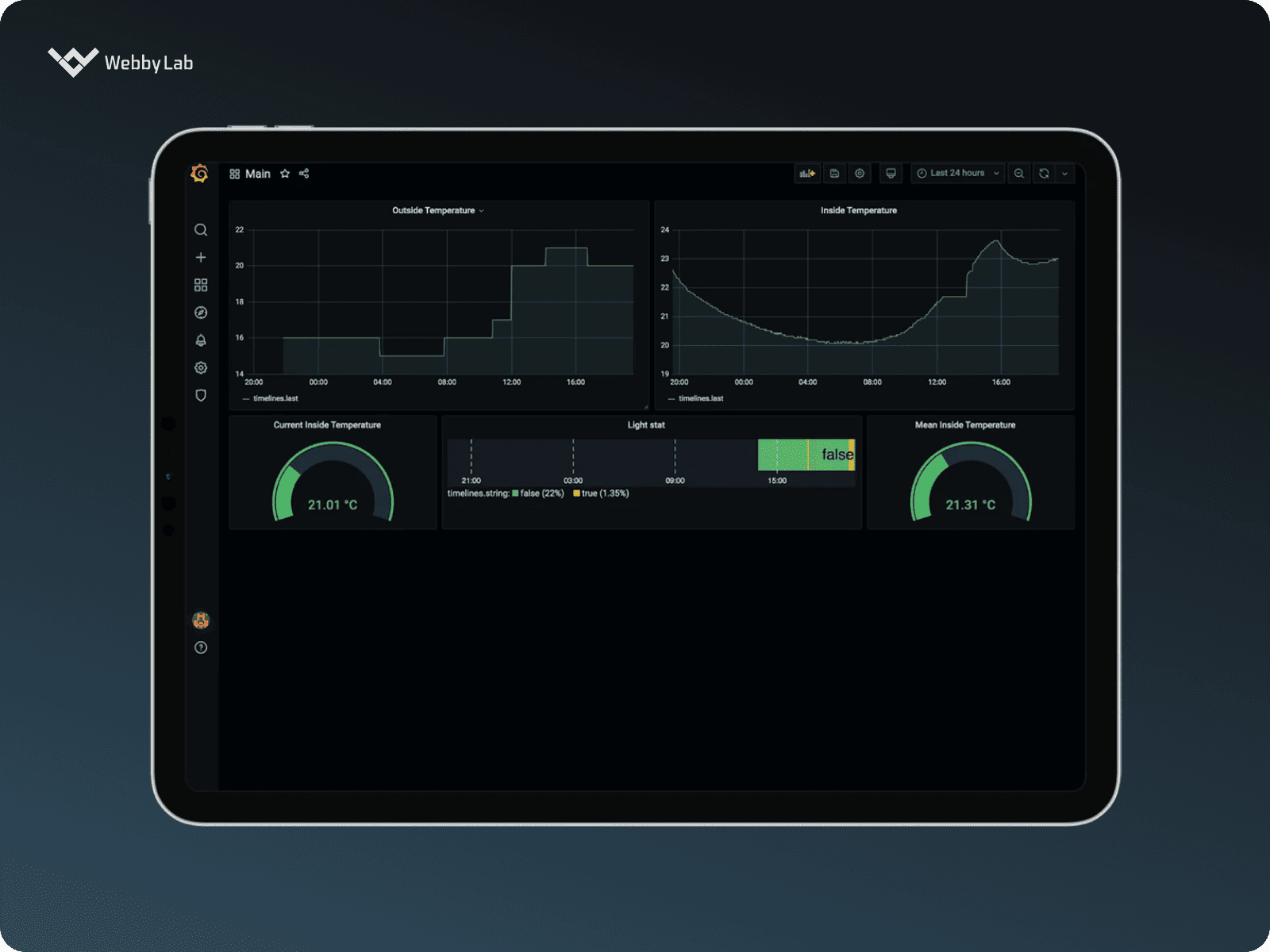 A smart greenhouse based on 2Smart Standalone
A smart greenhouse based on 2Smart Standalone



