From Layers to Components: IoT Architecture Explained
Written by:

Kostiantyn Oliynyk
Head of IoT at Webbylab
With a robust academic background in Telecommunication Systems Engineering, I apply my knowledge to lead innovations in the IoT domain. Starting as the first team member in the newly formed IoT department at WebbyLab, I've spearheaded its growth, fostering the expansion into embedded and hardware development alongside our core software projects. My dedication lies in pushing the boundaries of IoT technology, fostering a culture of innovation and excellence that profoundly impacts our clients' operational success.
FAQ
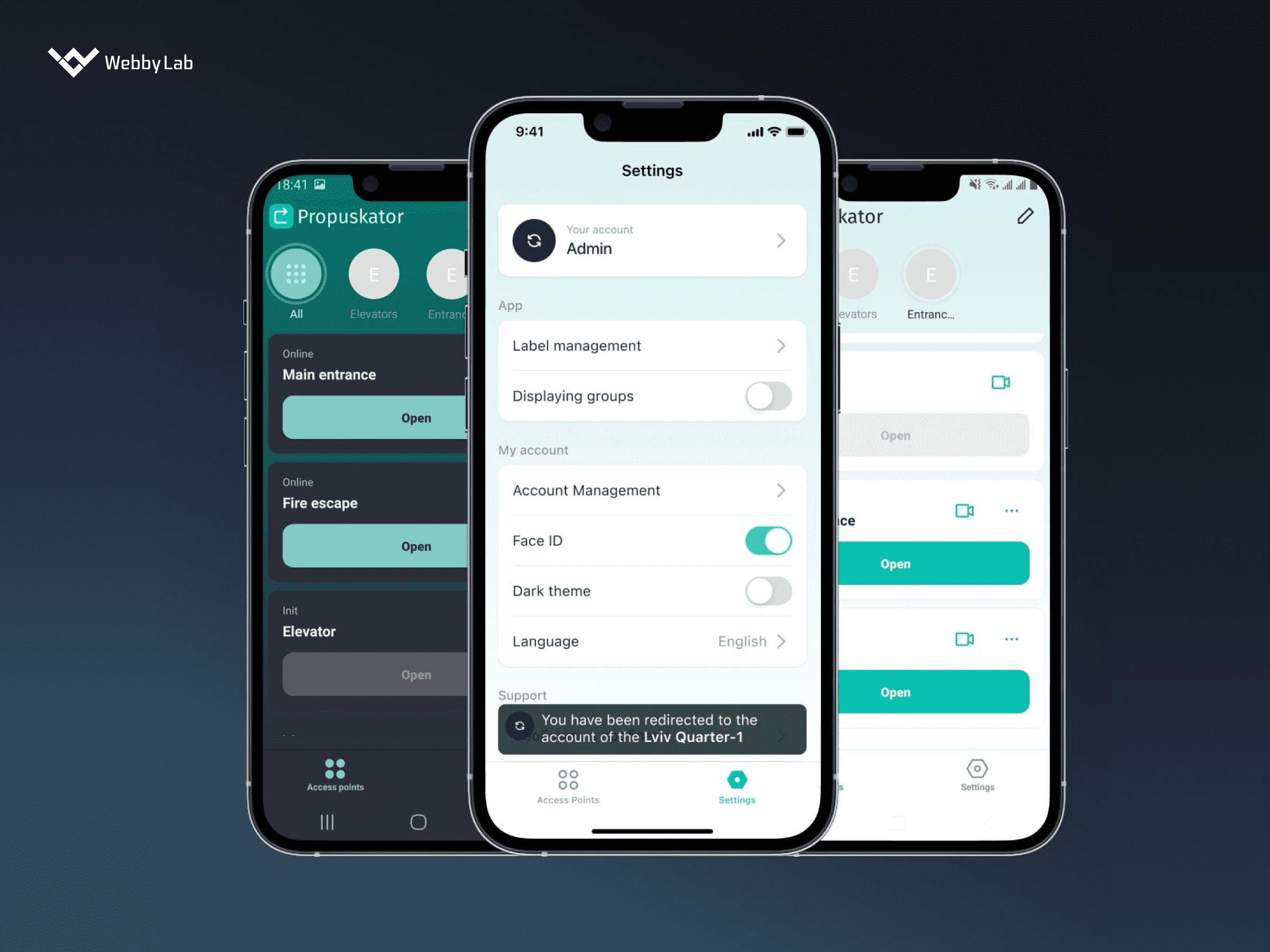
What is the role of the gateway in smart internet architecture?
In IoT end-to-end architecture, a gateway is an intermediary between the devices and the cloud. It facilitates bidirectional communication and seamless data flow.
What are the stages of creating an IoT architecture?
The typical stages of building an Azure IoT reference architecture or any other setup are:
- Installing IoT devices (sensors and actuators);
- Setting up the internet gateway;
- Establishing an edge IT system;
- Ensuring data centers and/or cloud storage.
At what stage of the IoT architecture are sensors used?
Sensors are used at the very first stage of the IoT architecture. They are installed throughout the facility to collect data on parameters like temperature, motion, light, and beyond.
What is the role of the cloud in the smart network architecture of the Internet of Things?
The cloud lets you store, process, and analyze data from IoT devices. It’s not only scalable and secure but also enables remote monitoring and management of devices. On top of that, it can be enhanced with machine learning algorithms and other tools for data analysis.
Which layer of the IoT architecture is responsible for aggregating and analyzing data from multiple devices?
The data processing and analysis layer is responsible for aggregating and analyzing data in industrial IoT architecture or any other solution. It often uses advanced analytics and machine learning algorithms to turn raw data into valuable insights.
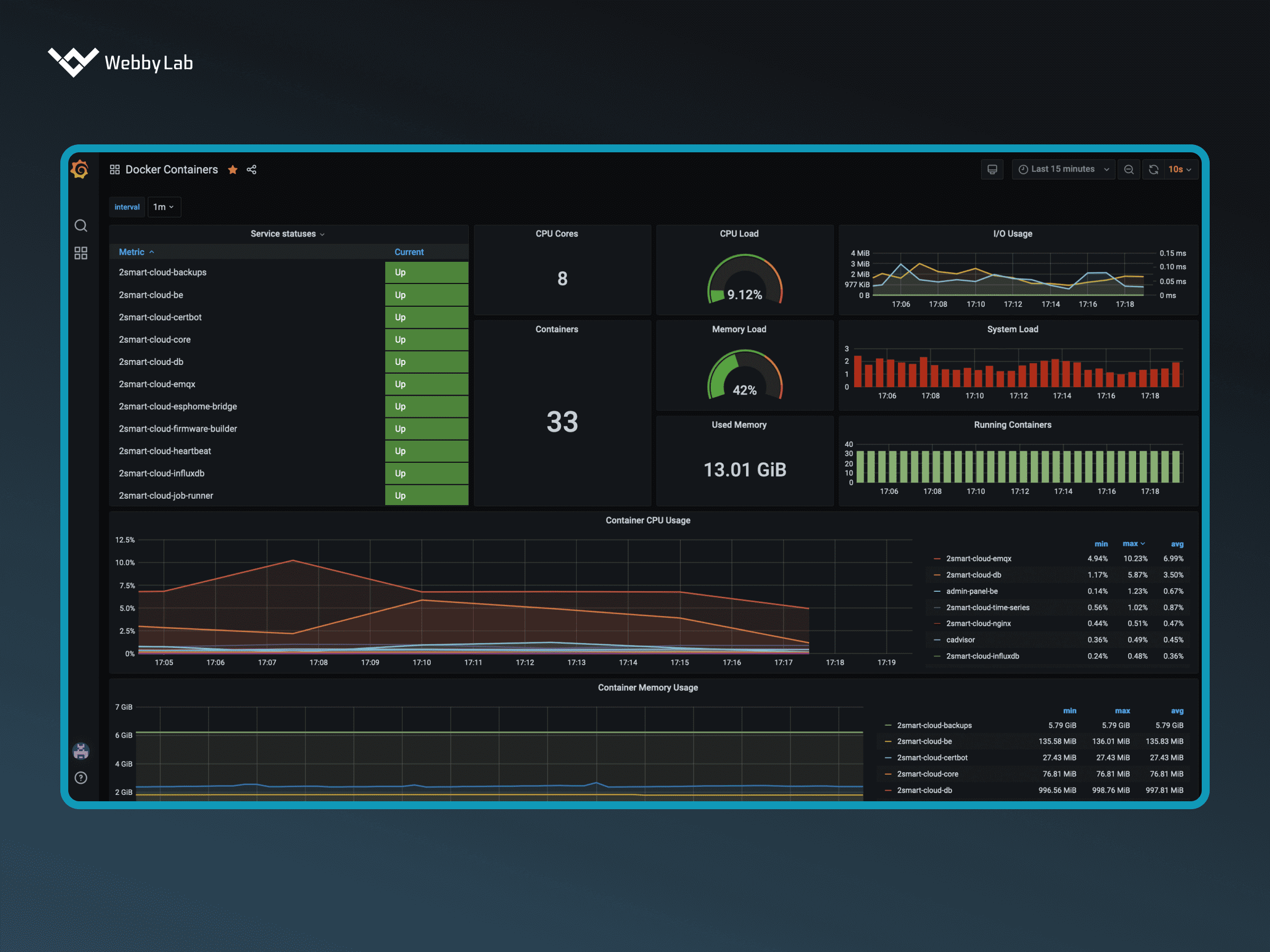
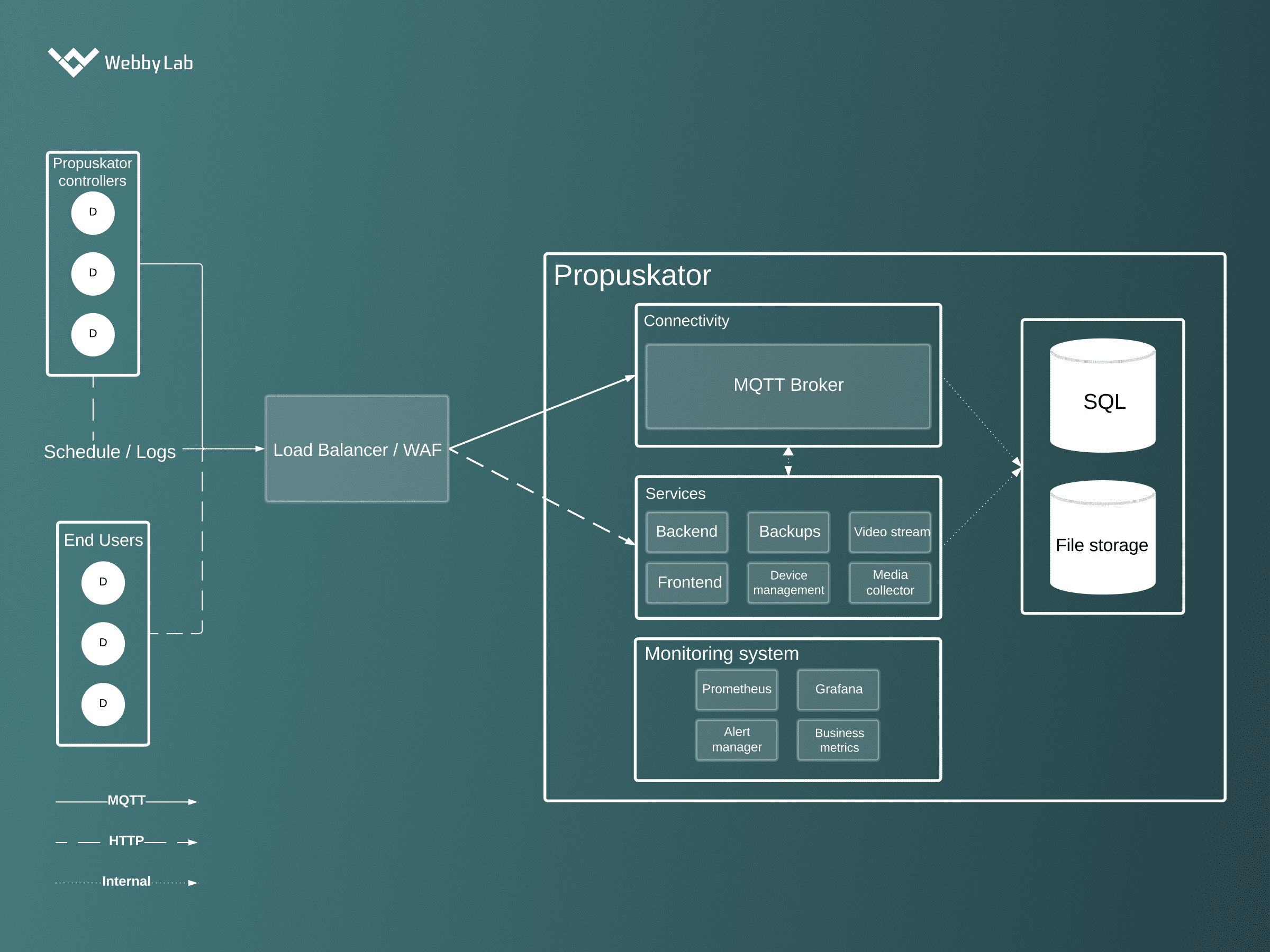
 The industries WebbyLab works with
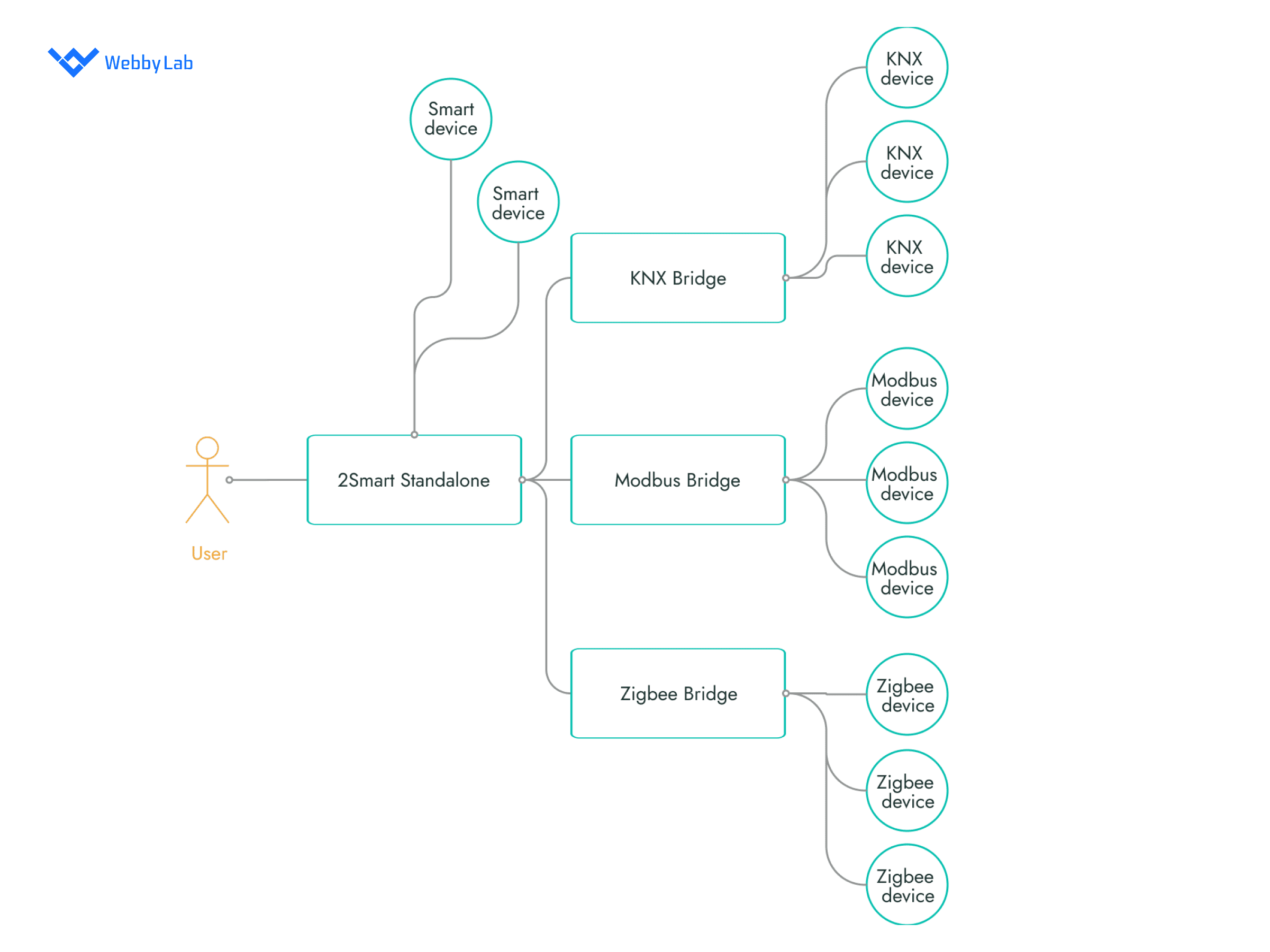
The industries WebbyLab works with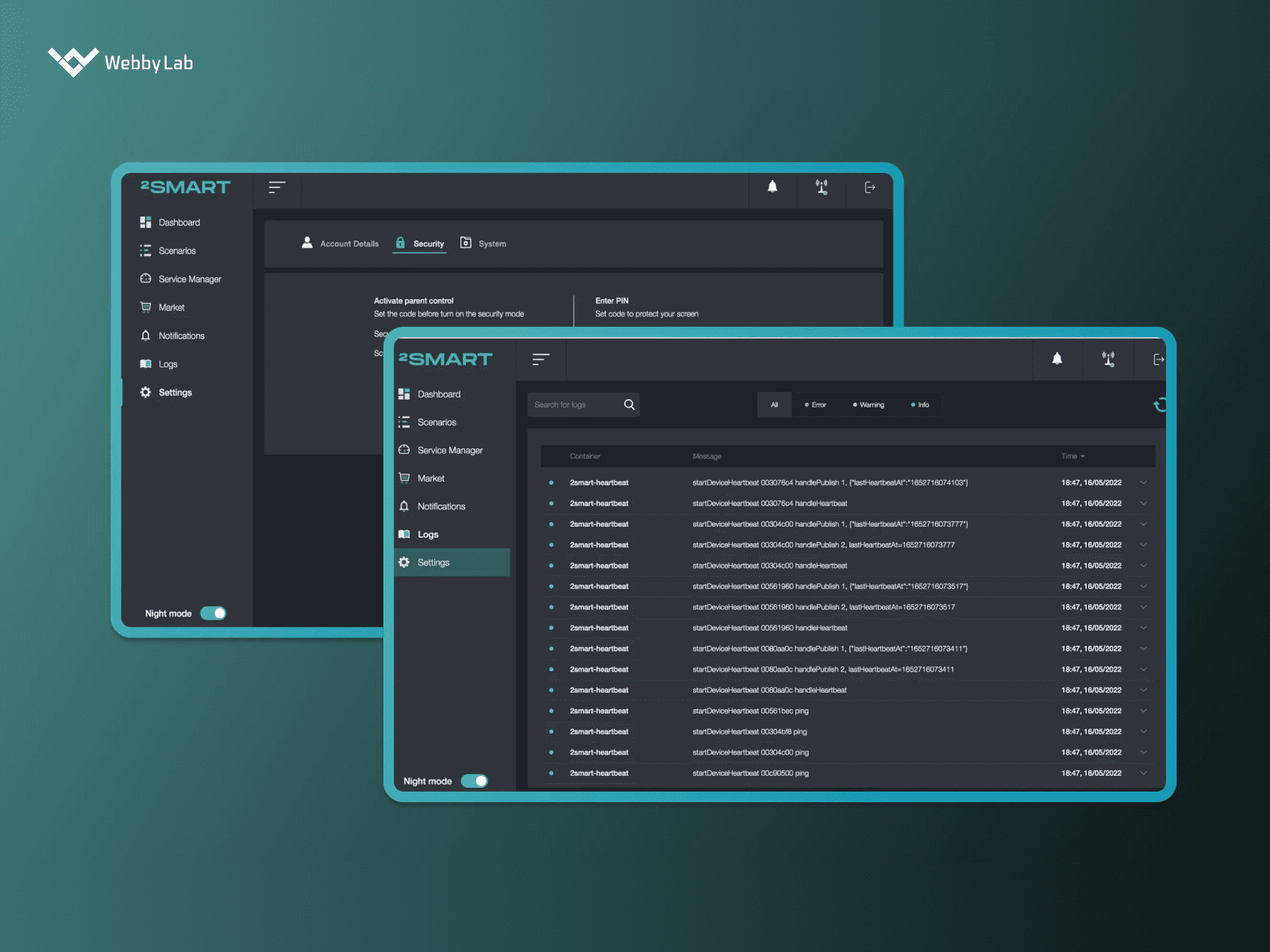 The 2Smart Standalone automation platform developed by WebbyLab
The 2Smart Standalone automation platform developed by WebbyLab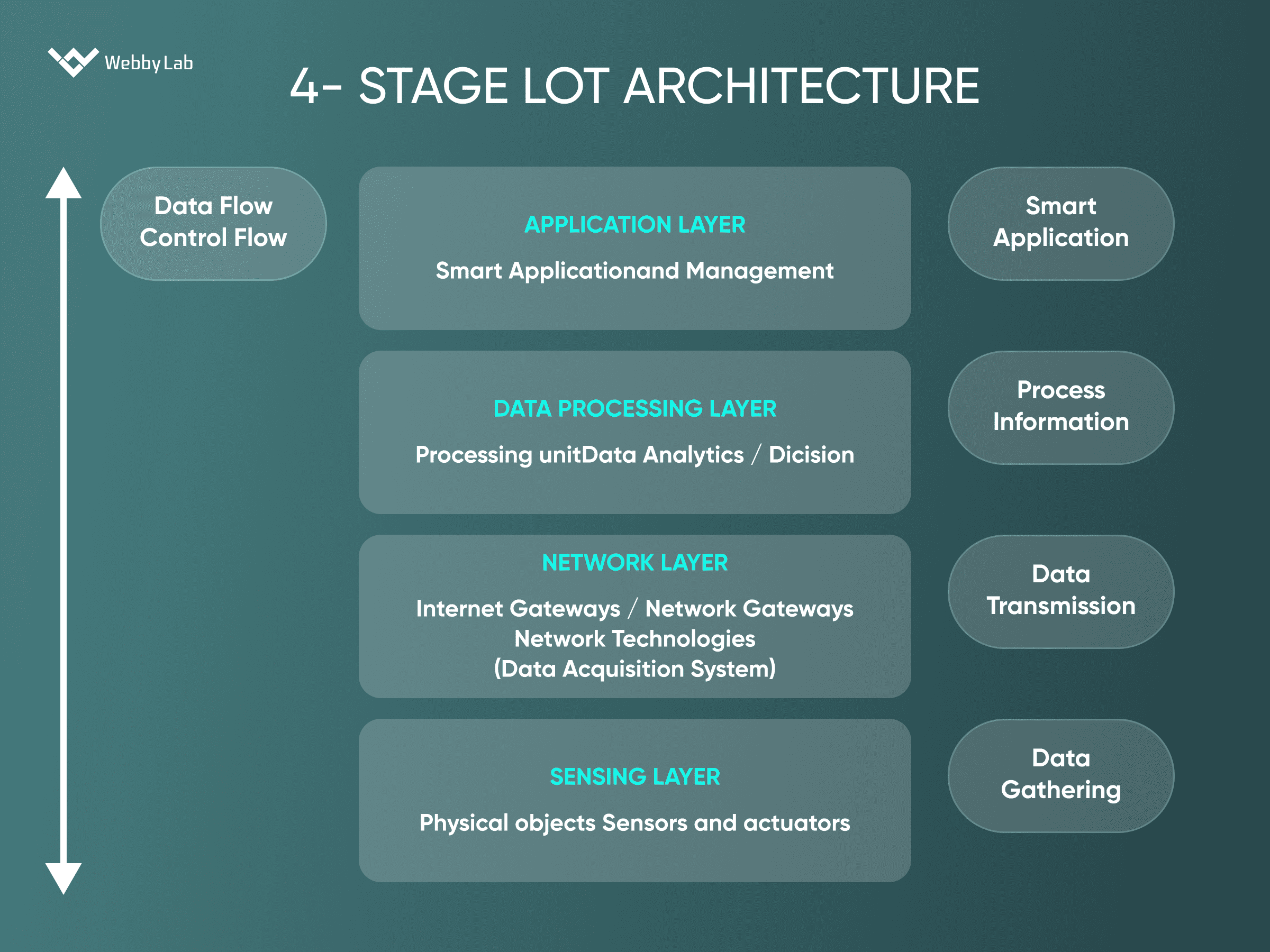
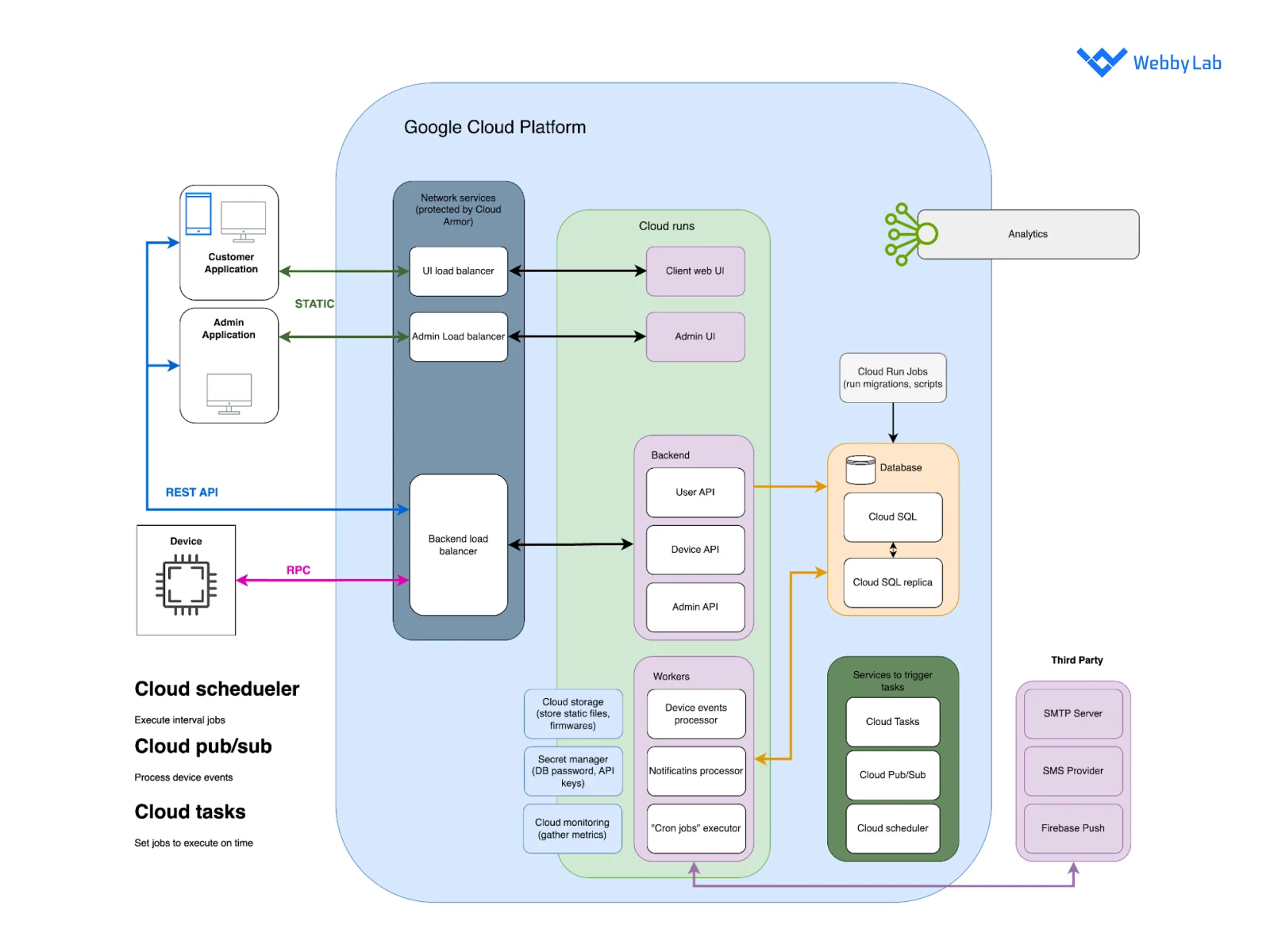
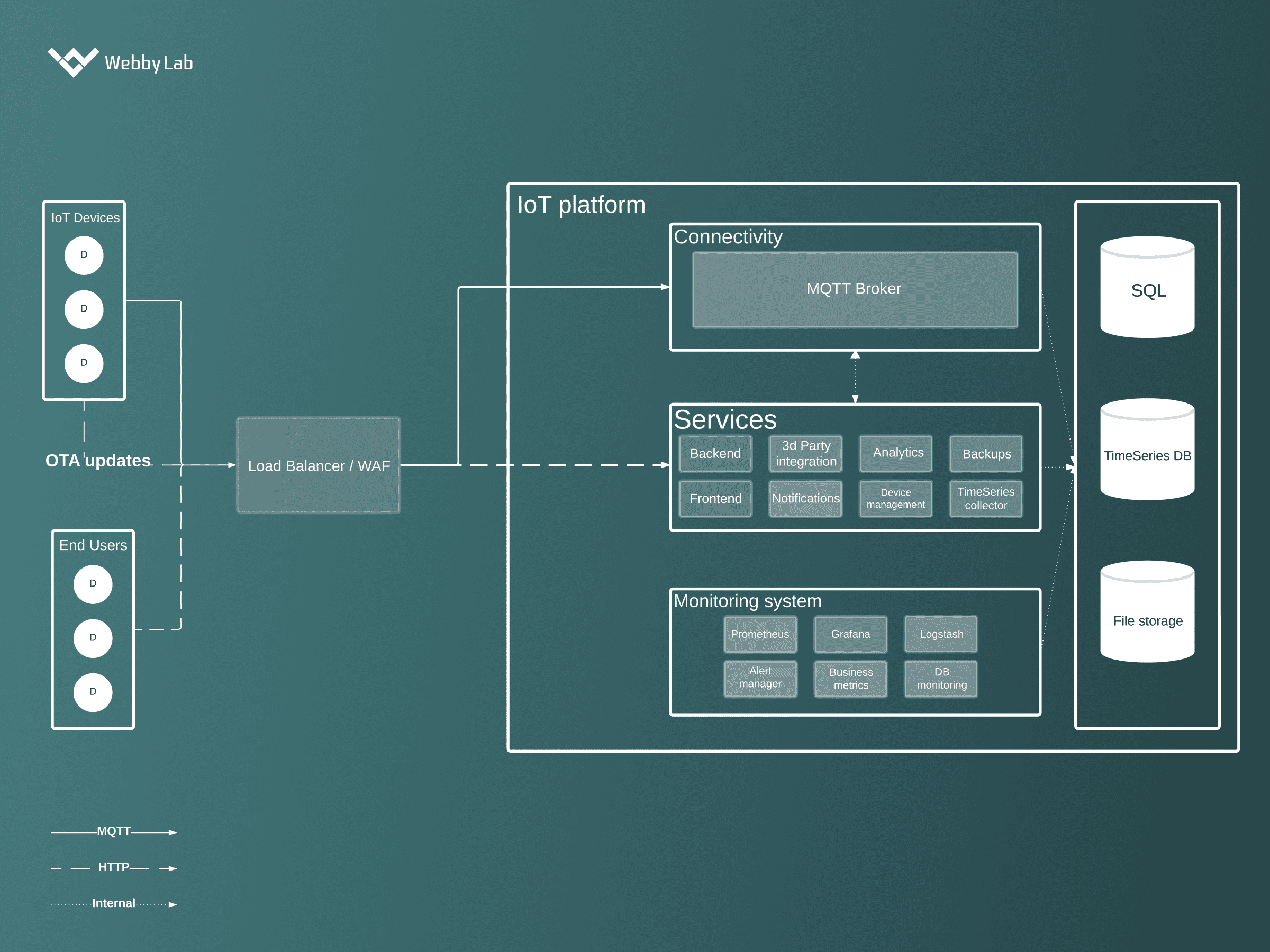 The diagram of a common IoT architecture
The diagram of a common IoT architecture