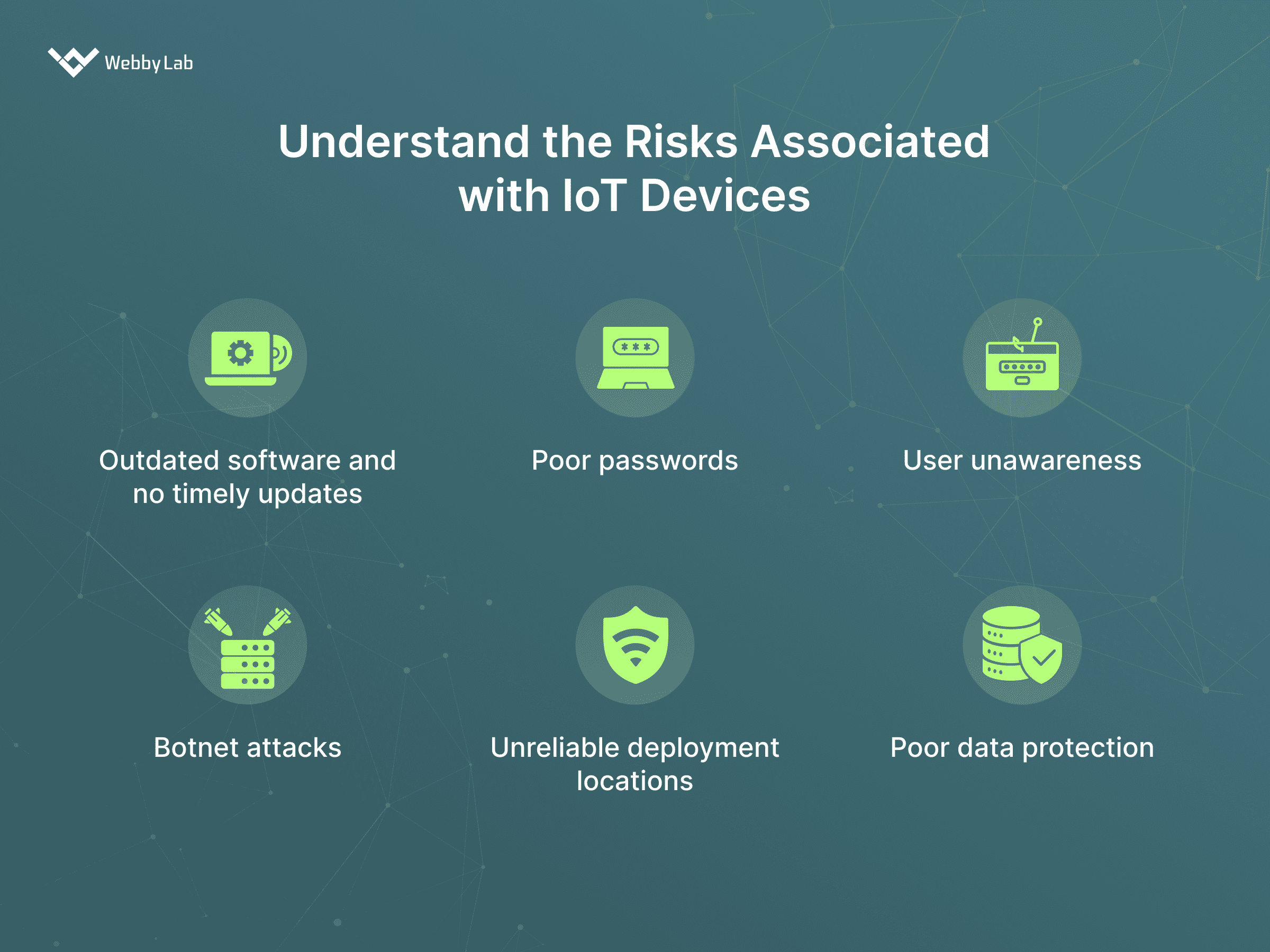
5 Essential Steps to Ensure Secure Communication with IoT Devices
Written by:

Kostiantyn Oliynyk
Head of IoT at Webbylab
With a robust academic background in Telecommunication Systems Engineering, I apply my knowledge to lead innovations in the IoT domain. Starting as the first team member in the newly formed IoT department at WebbyLab, I've spearheaded its growth, fostering the expansion into embedded and hardware development alongside our core software projects. My dedication lies in pushing the boundaries of IoT technology, fostering a culture of innovation and excellence that profoundly impacts our clients' operational success.
FAQ
How can VPNs ensure secure communication between IoT devices and other devices or networks?
VPNs encrypt the data transmitted between IoT devices and other networks. They route the traffic through a secure tunnel, protecting IoT gadgets from hacks, breaches, and unauthorized access.
How can users monitor their IoT devices to identify potential security breaches or vulnerabilities and ensure ongoing secure communication?
Users can handle device assessment through security software tools. Such software monitors network traffic and device activity. They can also enable logging features and ensure regular software and firmware updates. Finally, it’s worth tracking the device’s performance to detect unusual behavior.
What should I do if I suppose my IoT device has been compromised?
First, disconnect your IoT device from the network to prevent further damage. Next, change the device’s passwords and update the firmware and software to the latest version. Also, scan your IoT ecosystem for any other potentially compromised devices and strengthen your security measures.
Can I rely solely on my IoT device’s built-in security features?
We don’t recommend relying only on built-in security features. They often fail to protect your system adequately. Instead, it’s better to use the tips and methods described in our post to deliver top-notch IoT security.