Basic Security Testing for Web Applications: Tools, Techniques, and Best Practices
Explore common vulnerabilities, basic tools and best practices to keep your application safe from potential threats.

As the number of web applications grows, along with their crucial importance for businesses and everyday life, security becomes a primary concern in software development. The impact of losing confidential data or experiencing a system breach extends far beyond financial and reputational harm – it can affect many lives. So, how can you confidently protect your web application if you’re uncertain about where it might be vulnerable?
This question underscores the need to prioritize security testing early in the development lifecycle. It is a important element in ensuring that your web applications remain both reliable and secure. In this article, we will identify common vulnerabilities, outline methods for detecting them, and offer practical advice on how to enhance the security of your website.
Common Security Vulnerabilities
When securing web applications, it’s essential to be aware of the most common vulnerabilities that attackers exploit. The Open Web Application Security Project (OWASP) is a key resource that outlines critical risks and provides guidelines to mitigate them. The following recommendations are based on OWASP’s insights and highlight some of the most prevalent vulnerabilities, along with practical tips for testing them.
Maksym Lesnikov
Chief Technology OfficerHelped dozens of startups create effective digital products.
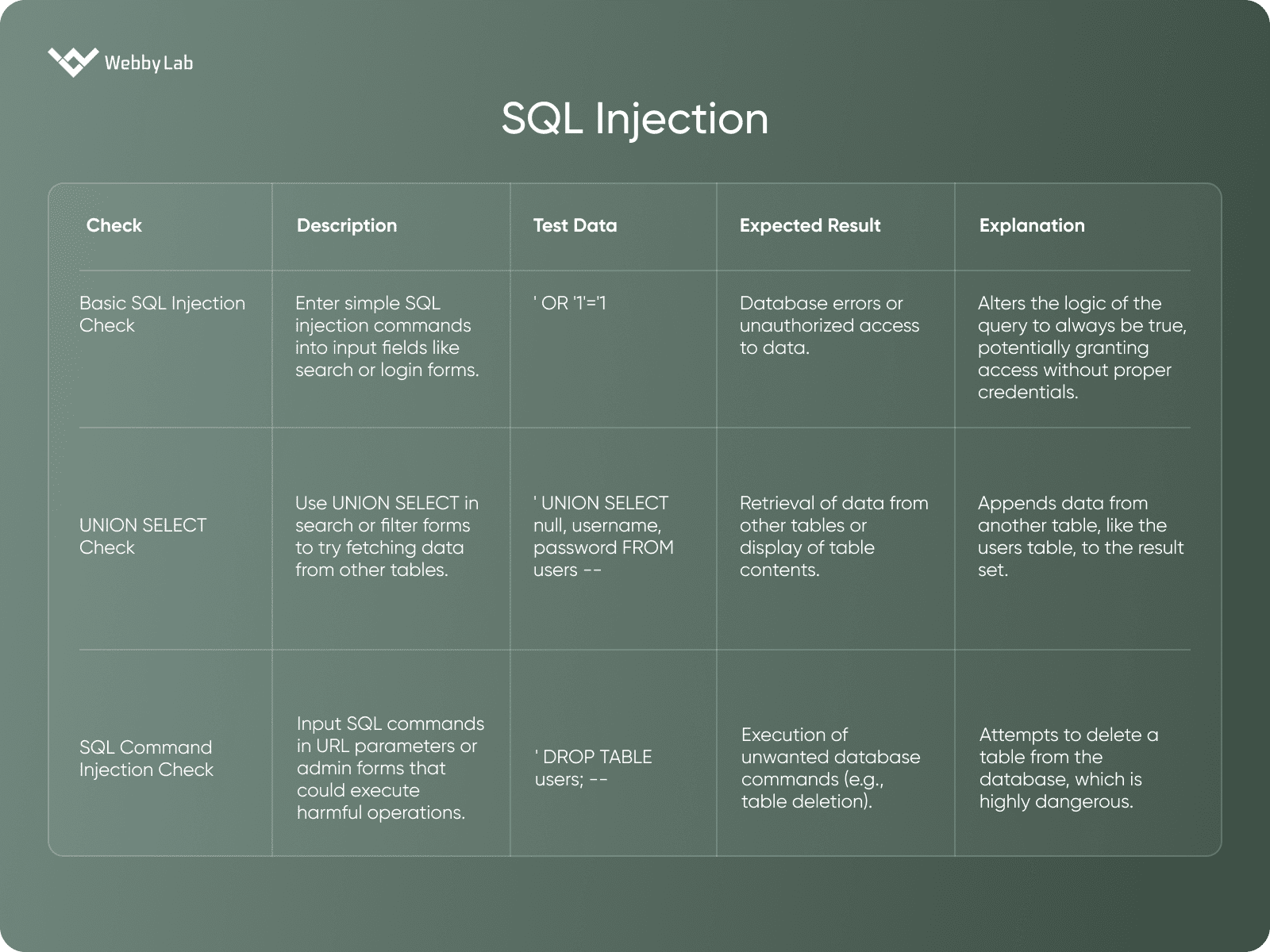
Get a ConsultationSQL Injection
A vulnerability that occurs when an attacker is able to execute arbitrary SQL queries in a web application’s database, often by manipulating input fields.
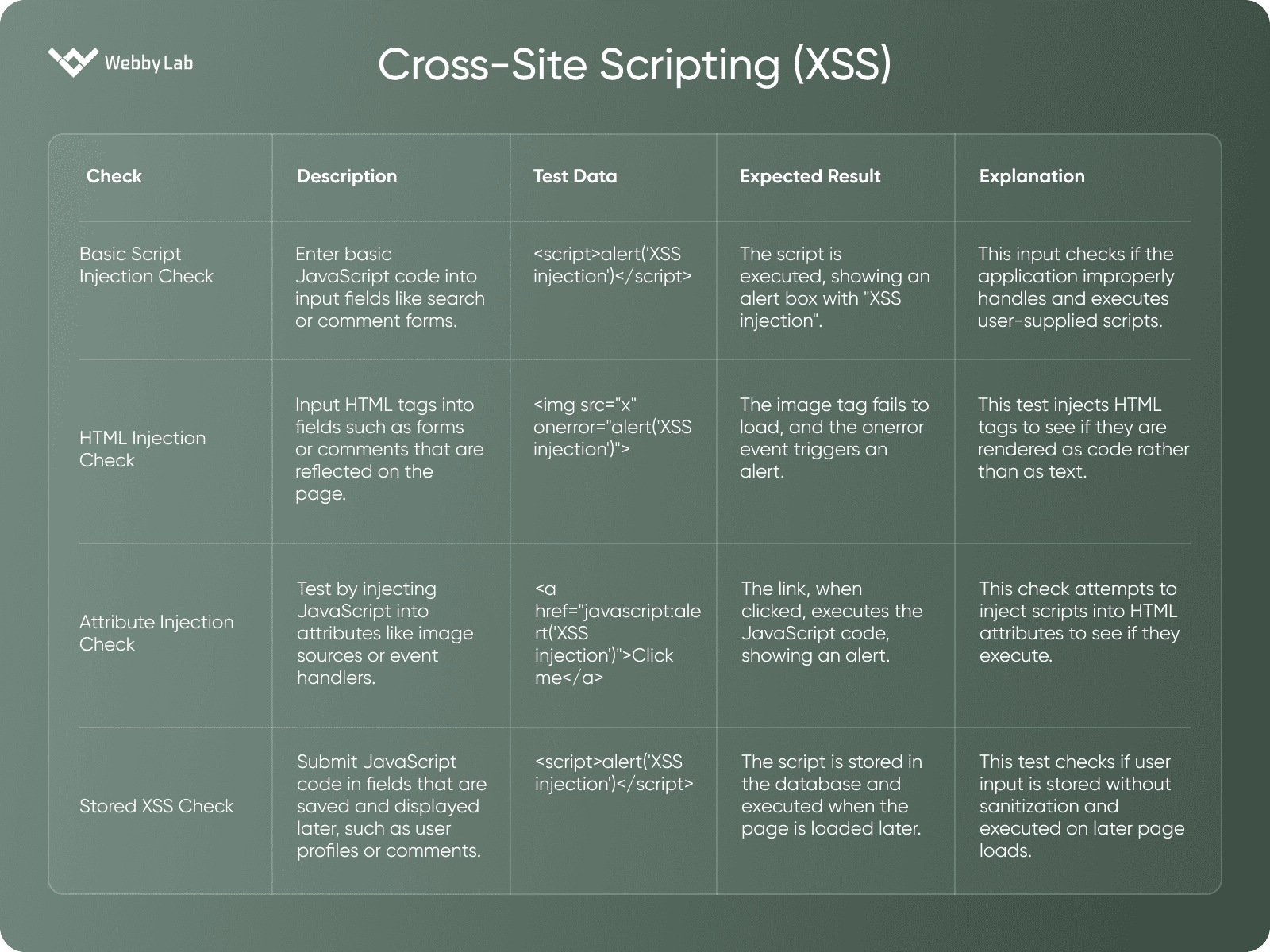
Cross-Site Scripting (XSS)
A vulnerability that allows attackers to inject malicious scripts into web pages viewed by other users, potentially leading to unauthorized actions or data theft.
Security Misconfiguration
A vulnerability arising from incorrect or insufficient configuration of security settings in an application, server, or database, making it more susceptible to attacks.
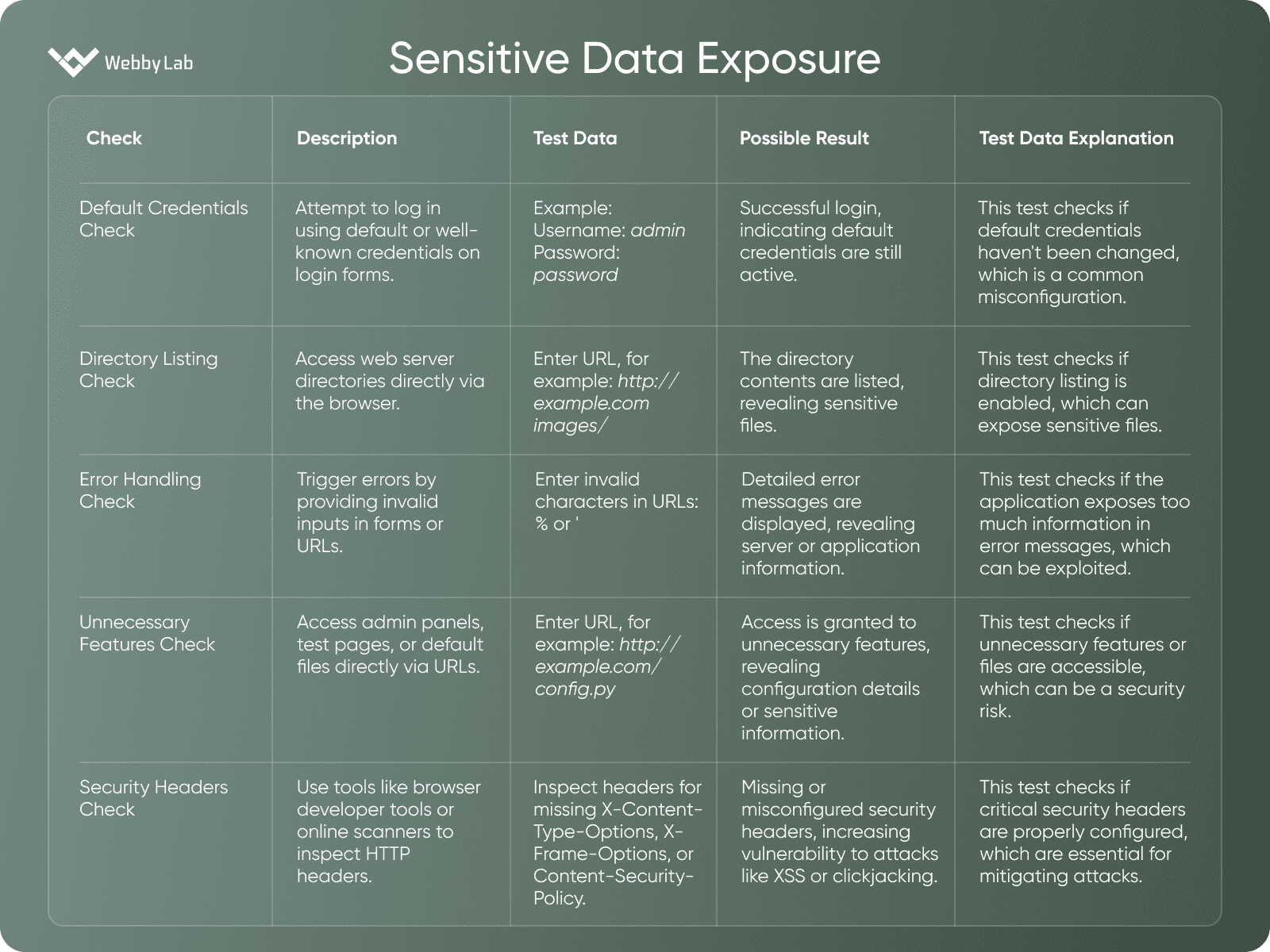
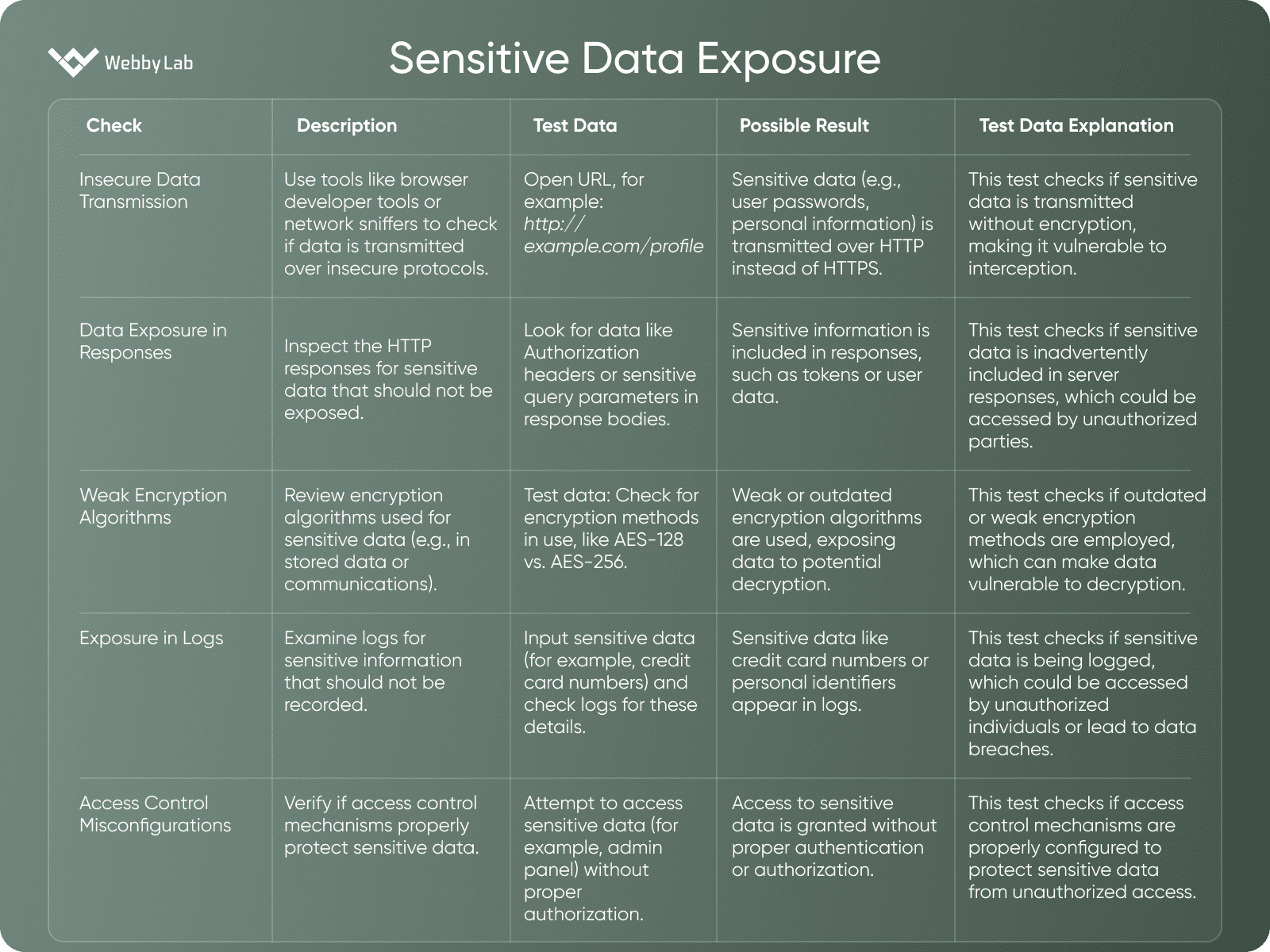
Sensitive Data Exposure
A vulnerability where sensitive data, such as personal or financial information, is exposed to unauthorized individuals due to inadequate protection measures.
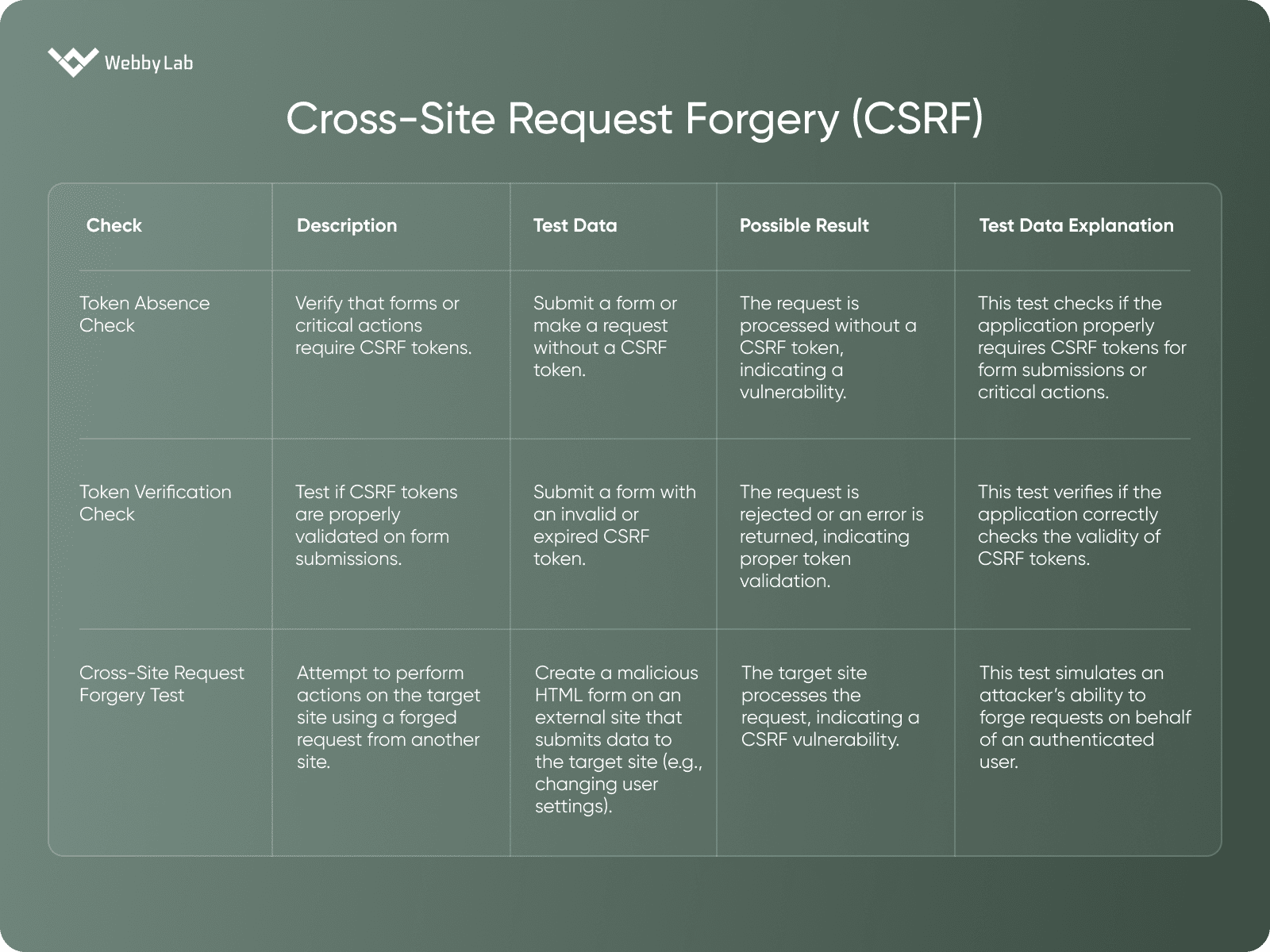
Cross-Site Request Forgery (CSRF)
A vulnerability that allows attackers to trick users into making unwanted actions on a web application where they are authenticated, potentially leading to unauthorized actions.
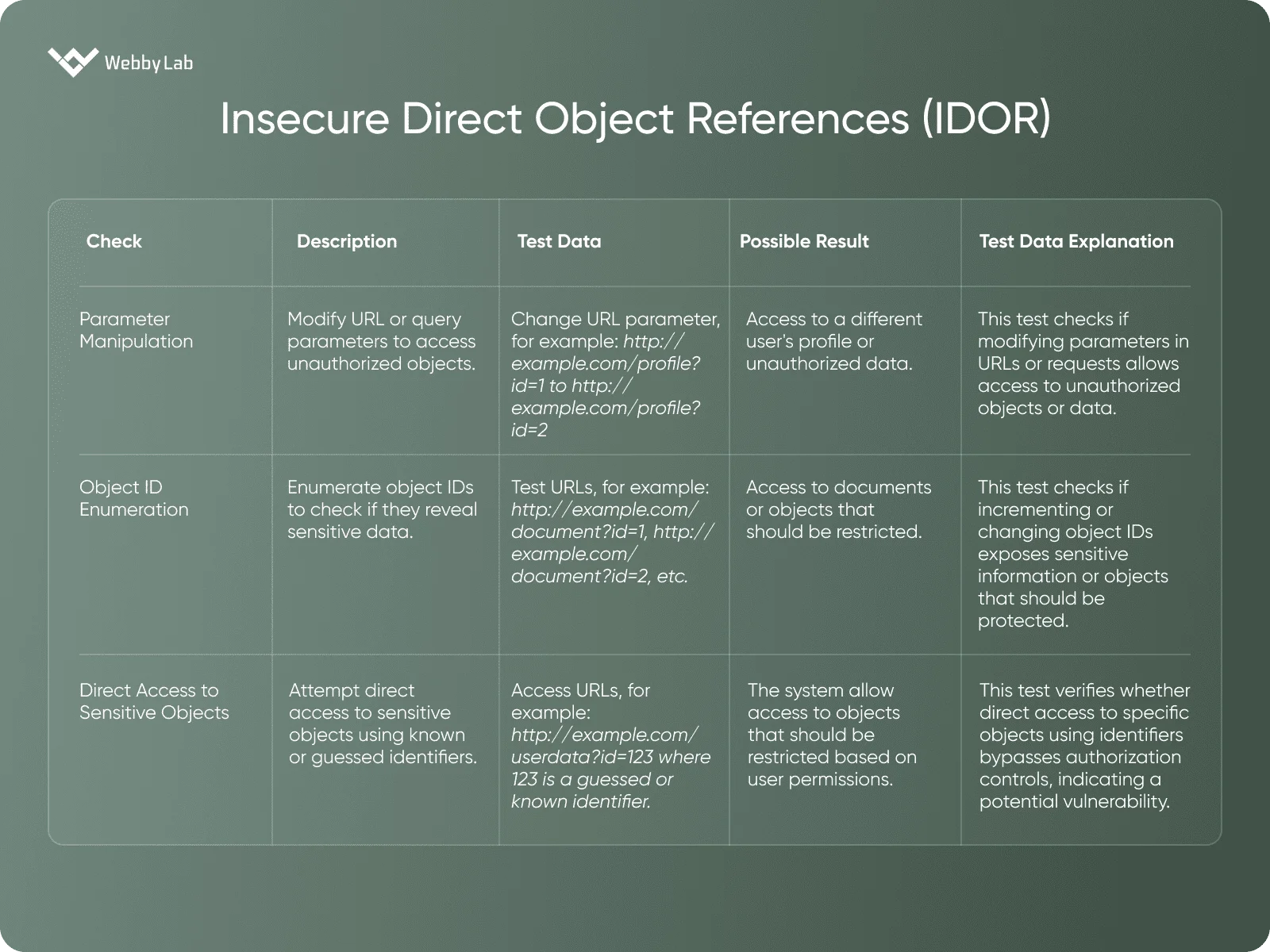
Insecure Direct Object References (IDOR)
A vulnerability where attackers can access or manipulate objects (e.g., files, database records) that they are not authorized to access by modifying input parameters.
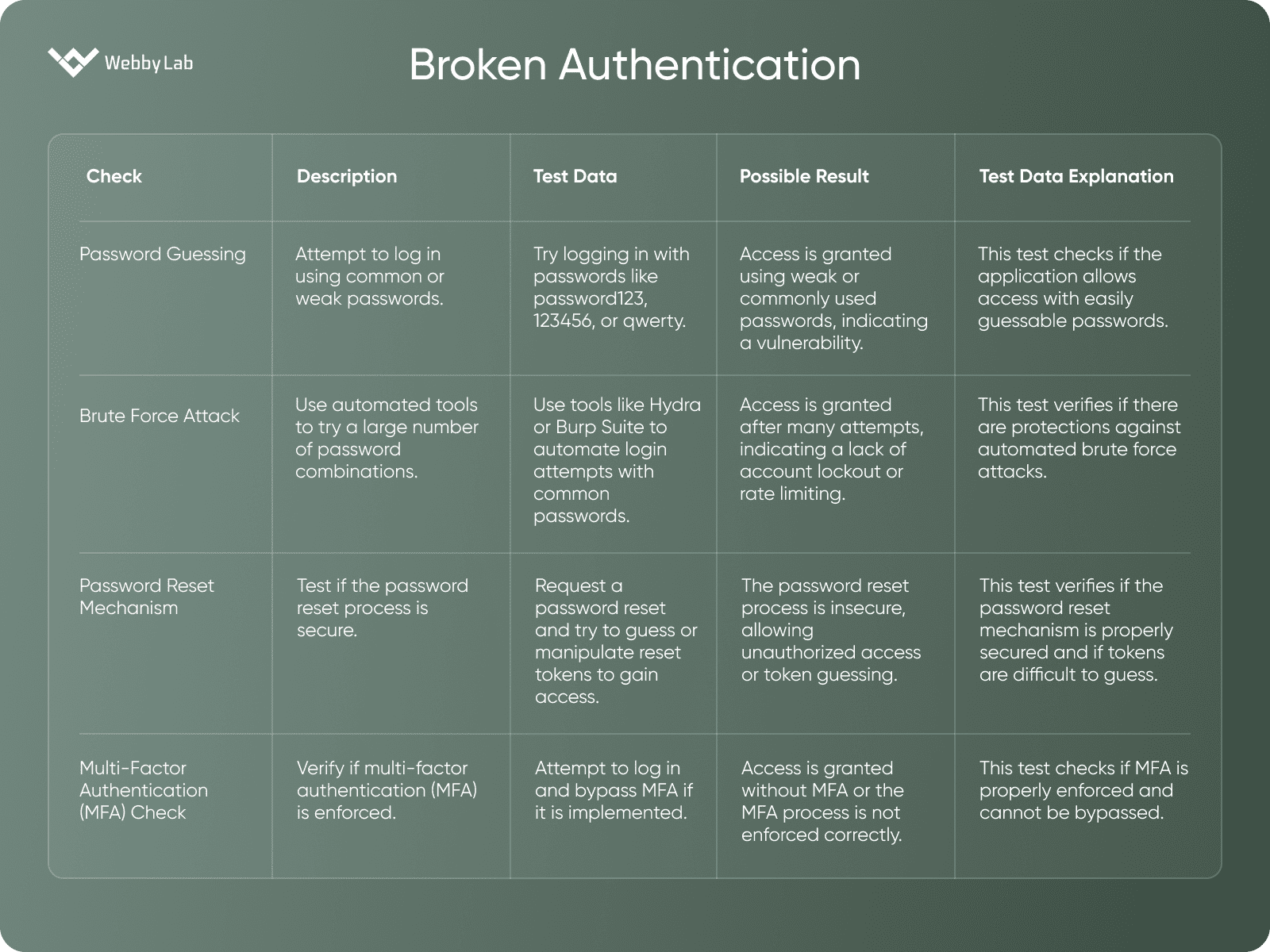
Broken Authentication
A vulnerability that occurs when authentication mechanisms are implemented incorrectly, allowing attackers to bypass authentication or gain unauthorized access.
Explore our portfolio with software development best practices to see how our team helped businesses in digital transformation
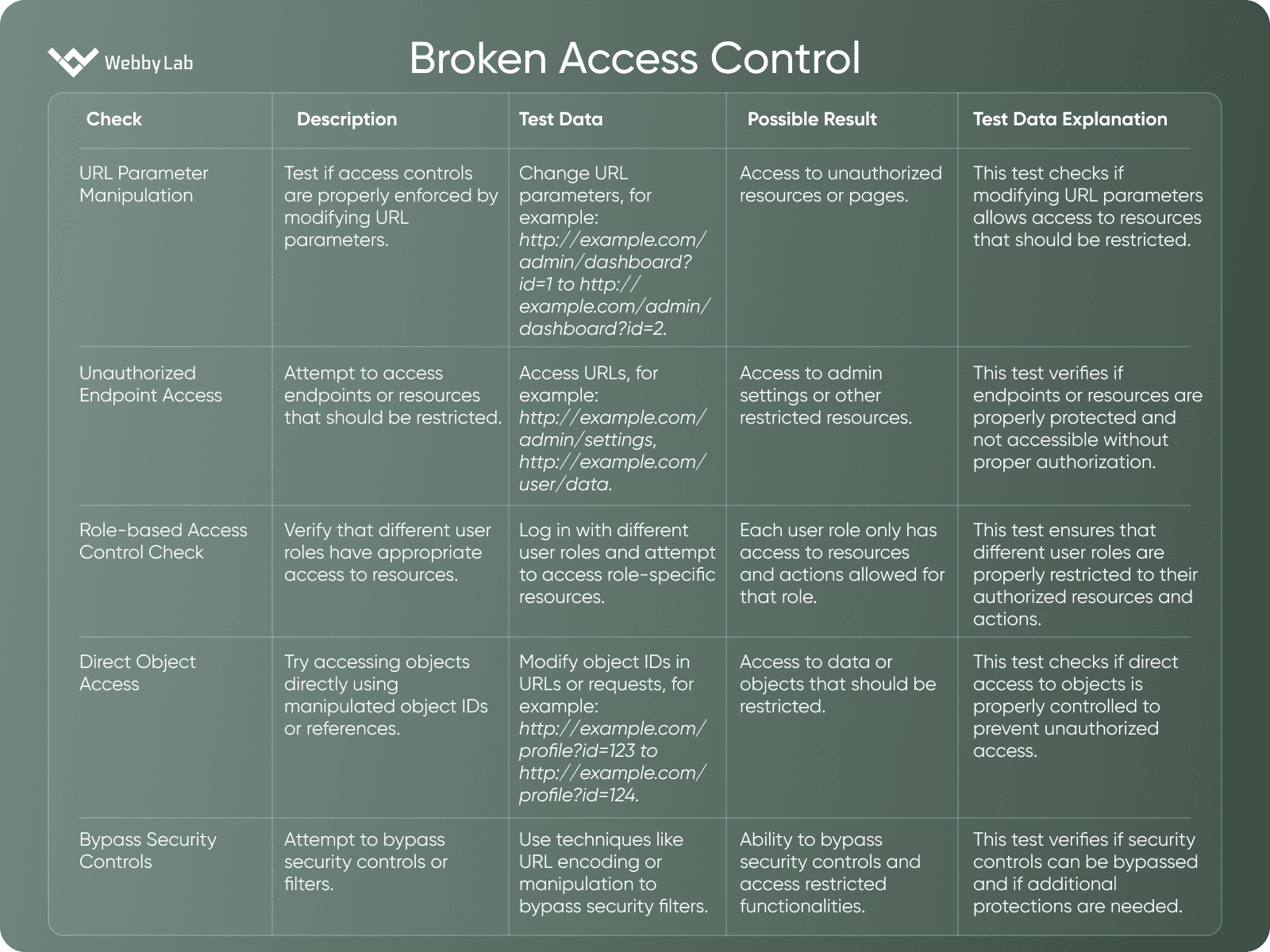
Uncover MoreBroken Access Control
A vulnerability where an application fails to properly enforce access controls, allowing unauthorized users to access or perform actions on resources that should be restricted.
Broken Access Control covers a wider range of access control issues compared to IDOR, despite sharing similar elements like URL manipulation. While IDOR specifically involves unauthorized access to particular objects through parameter manipulation, Broken Access Control addresses more general failures in enforcing access controls, allowing unauthorized actions or resource access.
After considering the common vulnerabilities, it is very important to take a systematic approach to security testing. A comprehensive security testing strategy should not only address these specific vulnerabilities, but also assess the overall security reliability of the web application.
Tools for Security Testing
Security testing tools play a critical role in automating and streamlining the identification of vulnerabilities. Here are some popular tools to consider:
- OWASP ZAP (Zed Attack Proxy): ideal for scanning web applications for vulnerabilities, including XSS, SQL Injection, and other common issues.
- Burp Suite: a comprehensive tool for penetration testing and vulnerability analysis, offering features like a web spider, scanner, and intruder.
- Nmap: useful for network exploration and security auditing, including port scanning and service detection.
- Nikto: a web server scanner that identifies outdated software, misconfigurations, and potential security issues.
- SQLMap: automates the detection and exploitation of SQL injection flaws, providing a powerful tool for testing and exploiting SQL injection vulnerabilities.
- Retire.js: detects outdated and vulnerable JavaScript libraries in your web application, helping identify potential security risks from outdated libraries.
- XXE Injection Tool: a specialized tool for detecting and exploiting XML External Entity (XXE) vulnerabilities in applications that process XML.
- Hydra: a fast and flexible network logon cracker that supports various protocols, useful for brute-force attacks on authentication systems.
- Wireshark: a network protocol analyzer that captures and inspects network traffic, helping identify vulnerabilities in data transmissions.
- SSL Labs: provides tools for testing the quality and security of SSL/TLS implementations, ensuring proper encryption and configuration of secure communications.
Basic Security Testing Checklist
To make your security testing easier, here’s a basic checklist that outlines the key areas of web application security. This checklist is intended to guide you through a structured process of identifying and remediating potential vulnerabilities:
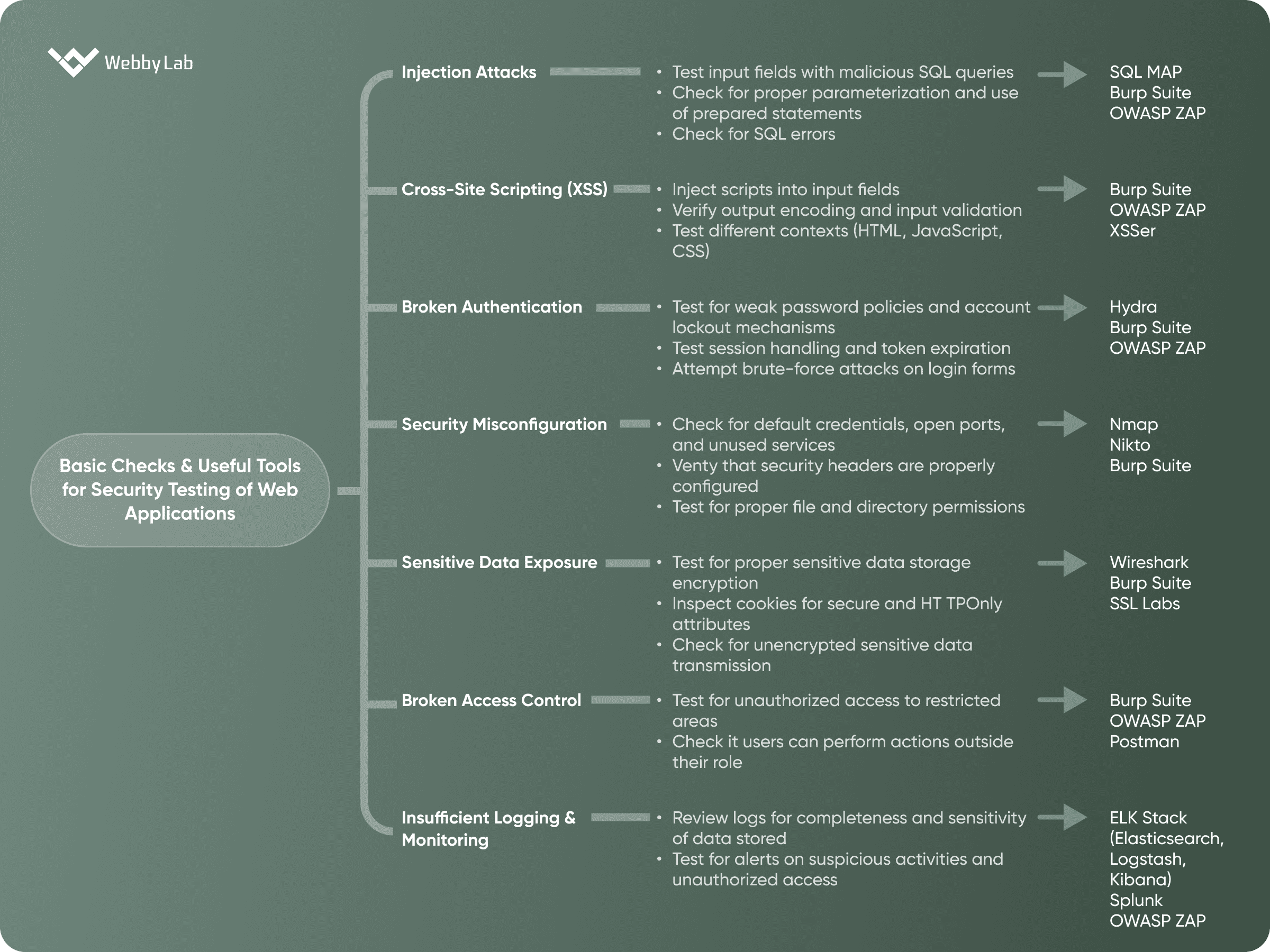
This checklist provides a foundation for your security testing efforts, but remember that each web application may have its unique vulnerabilities. It’s important to adapt your testing strategy to the specific needs and context of the application you are working on.
Leading Practices for Secure Web Applications
To build a resilient web application, consider implementing these best practices:
- Regular security audits: conduct frequent audits to identify new vulnerabilities.
- Secure coding practices: improve developer skills in secure coding and enforce security-focused coding standards.
- Continuous monitoring: integrate security testing tools into your CI/CD pipeline for ongoing protection.
- Early testing: integrate security testing in the early stages of development.
- Minimize sensitive information exposure: encrypt sensitive data and limit what’s exposed in logs and error messages.
- Access control: strictly enforce access controls based on roles and responsibilities.
- Don’t fall behind – stay updated: keep up with the latest security trends and regularly update your security measures.
Full-cycle development solutions tailored to your business needs. Let`s connect!
Find Out MoreClosing thoughts
In conclusion, security testing is a vital part of ensuring the safety and integrity of web applications. By understanding common vulnerabilities, following a structured testing checklist, utilizing the right tools, and adhering to best practices, developers along with QA engineers can significantly enhance the security of the applications they work on, protecting both the application and its users from potential threats. Additionally, for custom IoT development solutions, security testing becomes even more critical, as IoT devices often handle sensitive data and operate within interconnected environments, making them potential targets for cyber threats.
Rate this article !
34 ratingsAvg / 5




